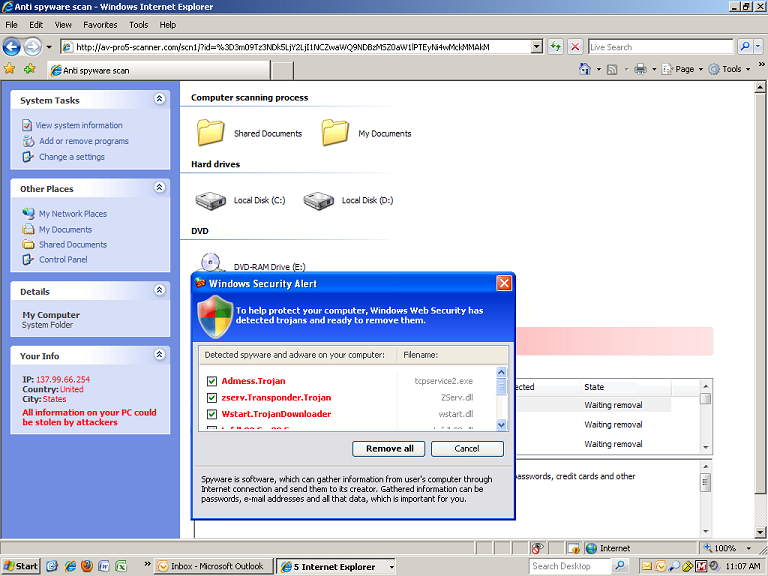
Downloader coming from tdss sites
VirusTotal
http://www.virustotal.com/analisis/853f ... 1269148478
Contains inside list of malware to download and self-deletion code.
VirusTotal
http://www.virustotal.com/analisis/853f ... 1269148478
Contains inside list of malware to download and self-deletion code.
> nul
/c del
COMSPEC
%skzwtguher.php?adv=adv447&code1=%s&code2=%s&id=%d&p=%s
%sddok.exe
%siolylzjjg.php?adv=adv447
%sbwadvg.exe
%sxekgqer.php?adv=adv447
%sstrcul.exe
%sekhrrfst.php?adv=adv447
%snxbtc.exe
%sybxliiv.php?adv=adv447
%splfyaqpj.exe
%swczjgtqqnk.php?adv=adv447
%snfylrs.exe
%sadmwk.php?adv=adv447
%svqaq.e
wZZ
Open
> nul
/c del
COMSPEC
%skzwtguher.php?adv=adv447&code1=%s&code2=%s&id=%d&p=%s
%sddok.exe
%siolylzjjg.php?adv=adv447
%sbwadvg.exe
%sxekgqer.php?adv=adv447
%sstrcul.exe
%sekhrrfst.php?adv=adv447
%snxbtc.exe
%sybxliiv.php?adv=adv447
%splfyaqpj.exe
%swczjgtqqnk.php?adv=adv447
%snfylrs.exe
%sadmwk.php?adv=adv447
%svqaq.exe
%stjgcdnnak.php?adv=adv447
%svqovnpnr.exe
%sgmvsjkh.php?adv=adv447
%slnfl.exe
%stfllijwxgu.php?adv=adv447
%sxsgv.exe
%setqrnbbym.php?adv=adv447
%sldrldu.exe
%syekhhiijfg.php?adv=adv447
%sbirqakky.php?adv=adv447
_hxxp://bastocks.com/maczjwtq/
_hxxp://aahydrogen.com/maczjwtq/
ver52
Ring0 - the source of inspiration