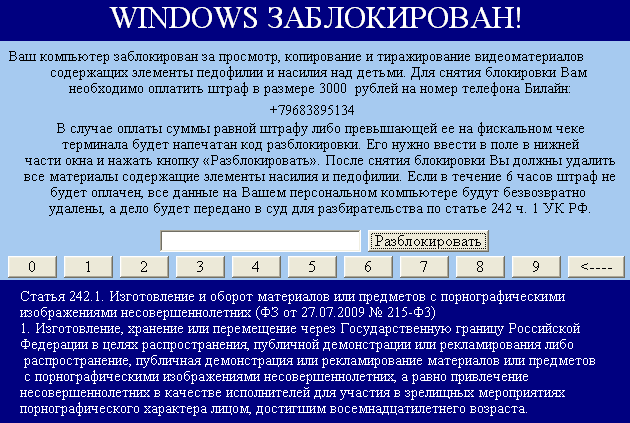
I think it bugged, as it impossible to enter correct deactivation code.

As for me, new appearance looks much better. Asks for ~65$ hm, inflation, I remember they started from ~15$ in 2011.
SHA1 07fd52bdc326d79c174d7ccd2e2cedb07e9ea3fb
https://www.virustotal.com/en/file/fe1a ... /analysis/
https://www.virustotal.com/en/file/6a7c ... /analysis/

As for me, new appearance looks much better. Asks for ~65$ hm, inflation, I remember they started from ~15$ in 2011.
SHA1 07fd52bdc326d79c174d7ccd2e2cedb07e9ea3fb
https://www.virustotal.com/en/file/fe1a ... /analysis/
https://www.virustotal.com/en/file/6a7c ... /analysis/
Attachments
pass: malware
(144.61 KiB) Downloaded 85 times
(144.61 KiB) Downloaded 85 times
Ring0 - the source of inspiration