EP_X0FF wrote:amanaksu wrote:I have been analyzing the current Moker. But this analysis has not been conducted because of anti-debugging. Why can not know that the failure of the part. Have you ever knows?
Use olly with antidebugging plugin. Everything described in above linked article.
First thanks for the reply.
As well as analysis on the blog before writing this article looked out all the information.
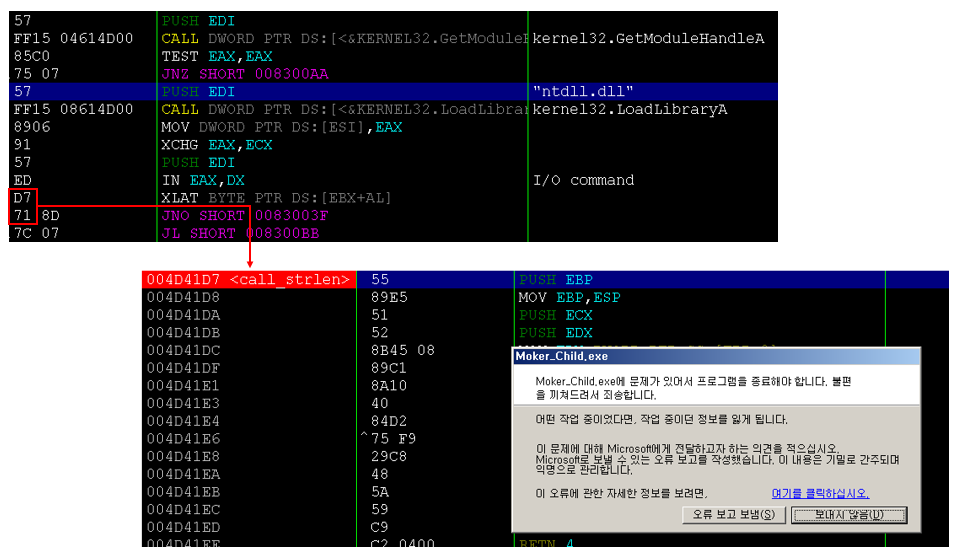
When the EIP has come to a position to run by VEH (figure on the 0x4D41DC) "Step into" exception occurs when you run and pops up a window like the one shown above.
I would wonder why if an exception occurs in normal code.
StrongOD used by the plugin.
Invite comments please.