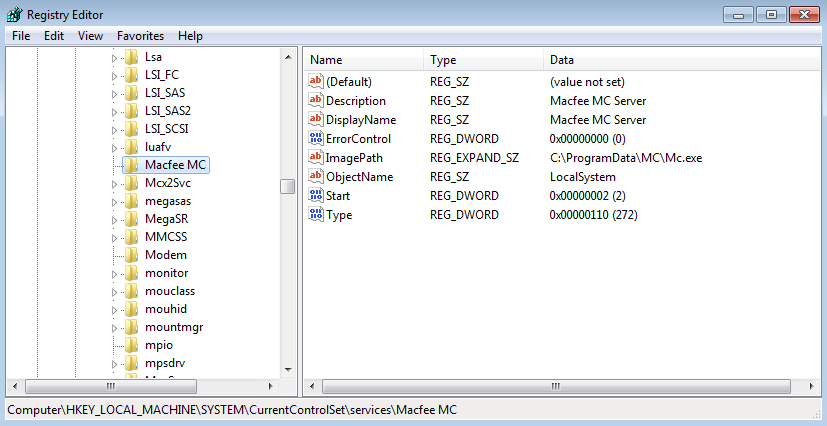
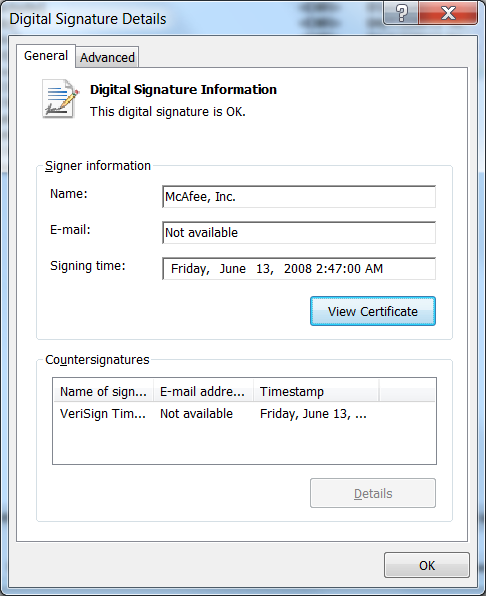
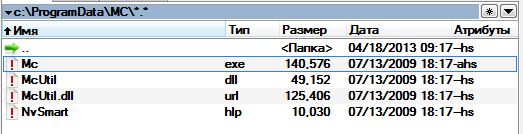
hi, im looking for
* MD5: f1f48360f95e1b43e9fba0fec5a2afb8
* SHA1: 70ceb467db7b0161d22e4545479f747417b9705a
* SHA-256: 2bc5ce39dd9afe2157448d3f6d8cb9c549ed39543d159616e38480b9e6c11c49
http://circl.lu/pub/tr-12/
http://circl.lu/files/tr-12/tr-12-circl ... sis-v1.pdf
* MD5: f1f48360f95e1b43e9fba0fec5a2afb8
* SHA1: 70ceb467db7b0161d22e4545479f747417b9705a
* SHA-256: 2bc5ce39dd9afe2157448d3f6d8cb9c549ed39543d159616e38480b9e6c11c49
http://circl.lu/pub/tr-12/
http://circl.lu/files/tr-12/tr-12-circl ... sis-v1.pdf