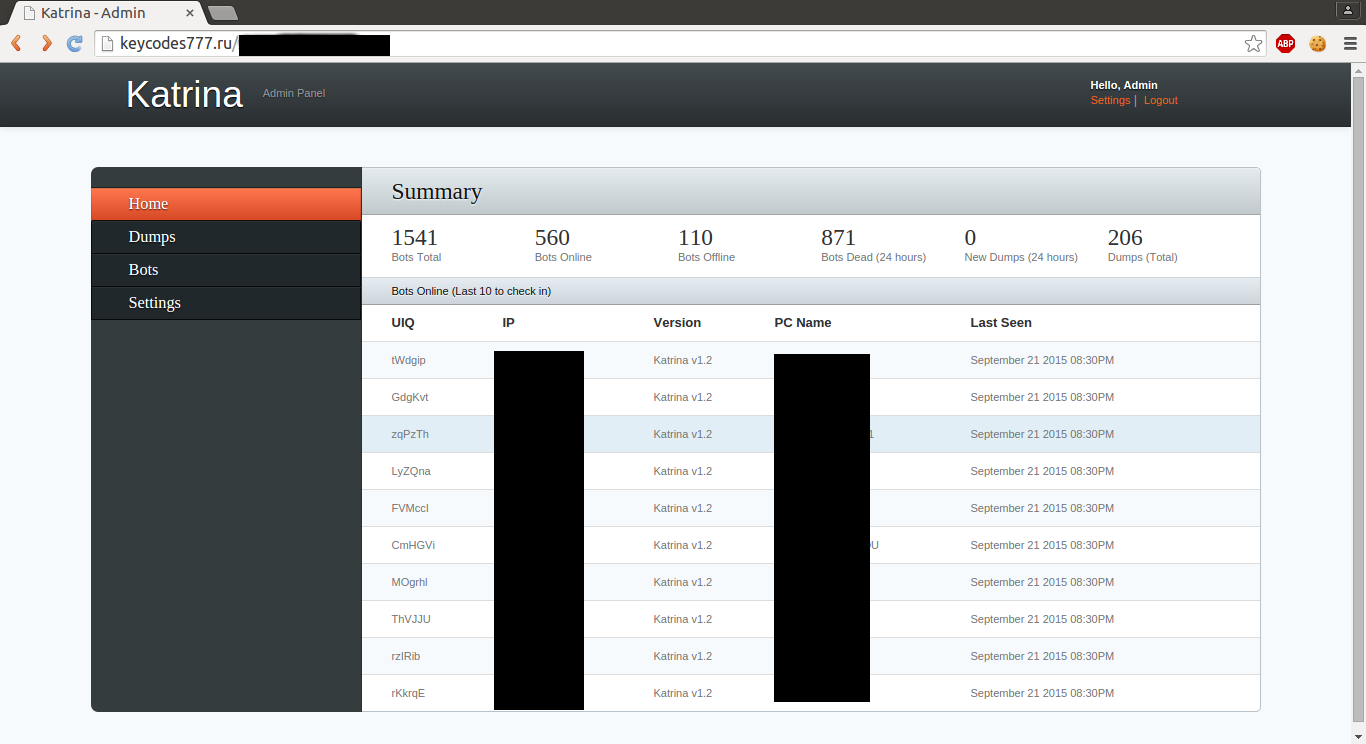
JackPOS (jack.exe) was hosted yesterday on the same place as NitlovePOS.
Panel located at 81.4.106[.]241/jack/admin.php?login=true
It has an interesting string :)
0x426000 (17): /jack/loading.php
0x426100 (12): 81.4.106.241
0x4261c0 (12): 81.4.106.241
0x426610 (114): if malicious use contact me xylitol@malwareint.com, don't hesitat! you can also use this string as flag signature.
Panel located at 81.4.106[.]241/jack/admin.php?login=true
It has an interesting string :)
0x426000 (17): /jack/loading.php
0x426100 (12): 81.4.106.241
0x4261c0 (12): 81.4.106.241
0x426610 (114): if malicious use contact me xylitol@malwareint.com, don't hesitat! you can also use this string as flag signature.
Attachments
infected
(191.02 KiB) Downloaded 104 times
(191.02 KiB) Downloaded 104 times