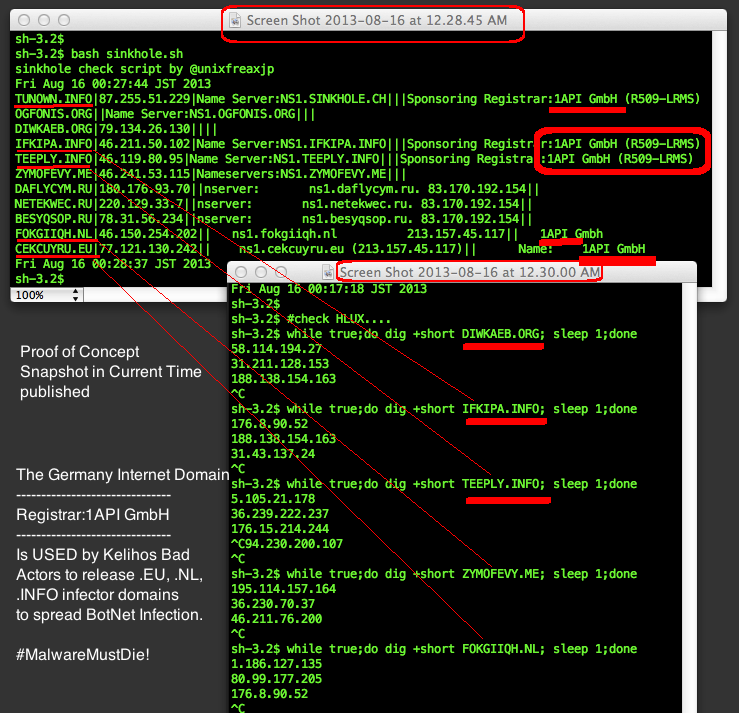
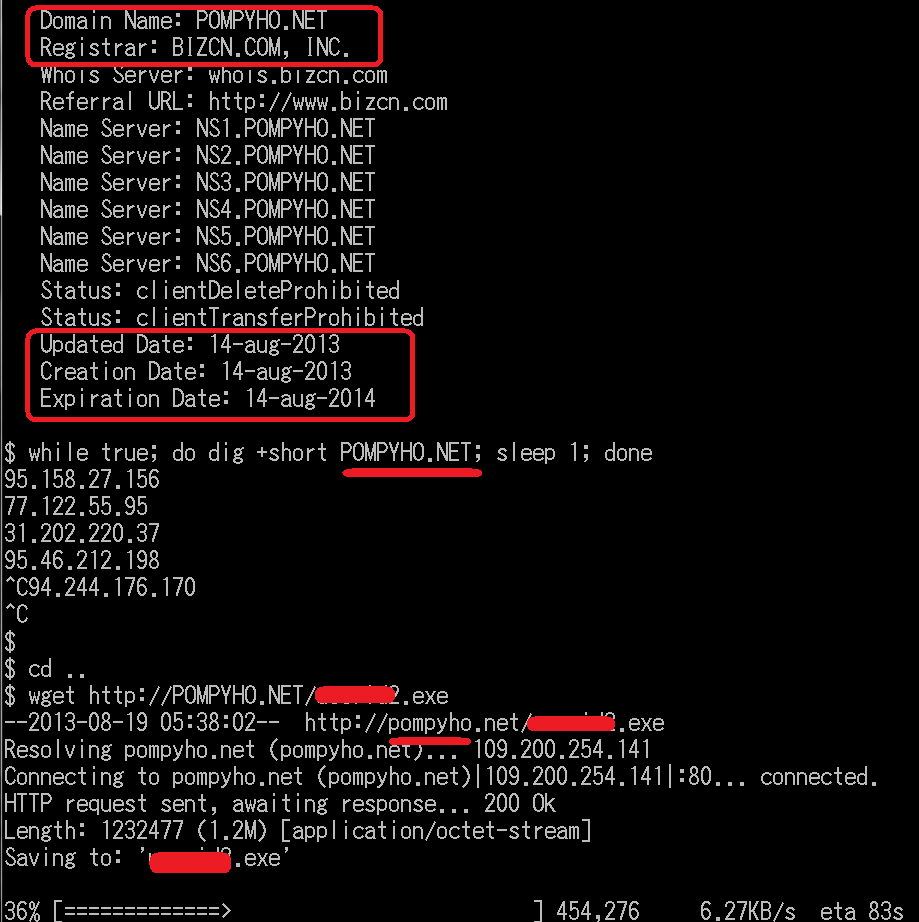
OP #Kelihos by #MalwareMustDie team.
Report is attached, for registered members only.
Read the comment before. Many mis-spell pls bear.
Please support us suppressing Kelihos and please help to cleanup IP infection in your network & country.
Report is attached, for registered members only.
Read the comment before. Many mis-spell pls bear.
Please support us suppressing Kelihos and please help to cleanup IP infection in your network & country.
Attachments
The attachment is text file contains report of the latest OP Kelihos status, shared to KERNELMODE.INFO exclusively.
The information is important to research/study purpose, suspension purpose, and mitigation purpose.
The information is free to use with mention MalwareMustDie group who made hard effort on this OP.
Any paste and claiming the research data for any forum online by any entity w/o mention is forbidden.
MalwareMustDie (here-forth MMD) is legal NPO entity registered in Ohio,US and Tokyo, Japan,
withhold rights of the current data and the abuse of usage will be legally prosecuted.
---
On behalf of MalwareMustDie, @unixfreaxjp
(4.58 KiB) Downloaded 63 times
The information is important to research/study purpose, suspension purpose, and mitigation purpose.
The information is free to use with mention MalwareMustDie group who made hard effort on this OP.
Any paste and claiming the research data for any forum online by any entity w/o mention is forbidden.
MalwareMustDie (here-forth MMD) is legal NPO entity registered in Ohio,US and Tokyo, Japan,
withhold rights of the current data and the abuse of usage will be legally prosecuted.
---
On behalf of MalwareMustDie, @unixfreaxjp
(4.58 KiB) Downloaded 63 times