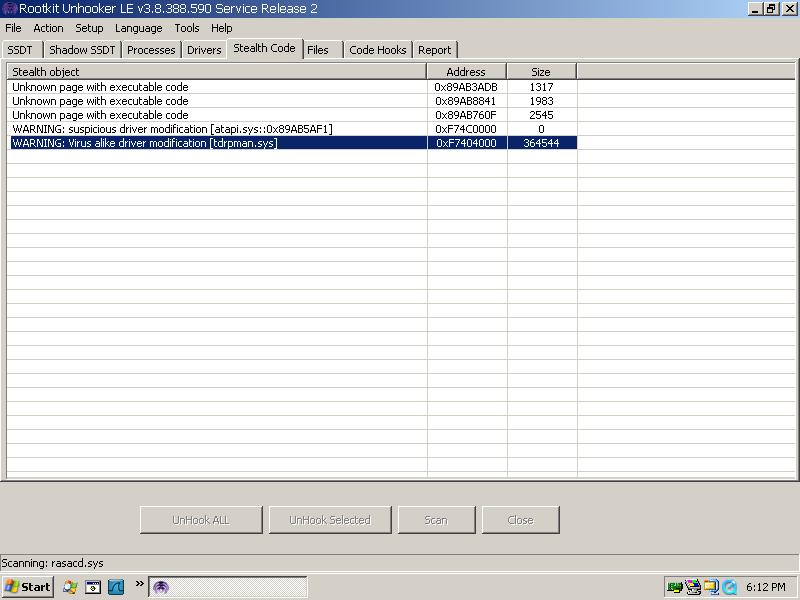
fatdcuk wrote:Another novel dropper, tested by proxy over messenger (Danke PX5 ;))Dropped a temp file with no extension which has the same md5 as loader.exe and a S5e55.dll at the same size but different md5.
http://www.virustotal.com/file-scan/rep ... 1283281751
This one needs to stew for a bit...
.
S5e55.dll - 10/43 - Dr Web - BackDoor.Tdss.4057
http://www.virustotal.com/file-scan/rep ... 1283296248