Ironically, I found AV "bypass" functionality in that crap.
Early samples have av name hash table
hash_table.png (2.08 KiB) Viewed 805 times
Old sample hash function:
Code: Select all for char_ in str_:
char_int = ord(char_)
hash_ = (rol(hash_,3) & 0xFFFFFFFF)
hash_ = (hash_&0xFFFFFF00)|((hash_&0x000000ff)^char_int)
Malware enumerate processes list and check presence of AV processes via hash table. If malware founds any AV processes, it launches process in suspended state and injects payload in it.
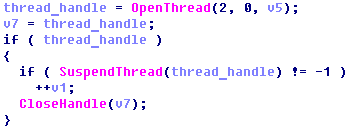
Injected payload code is again enumerating AV processes and suspends their threads.
dumb_code.png (2.64 KiB) Viewed 805 times
So basically it is a lame proxy injecting attack. In new samples AFAIK the hash table is cutted.