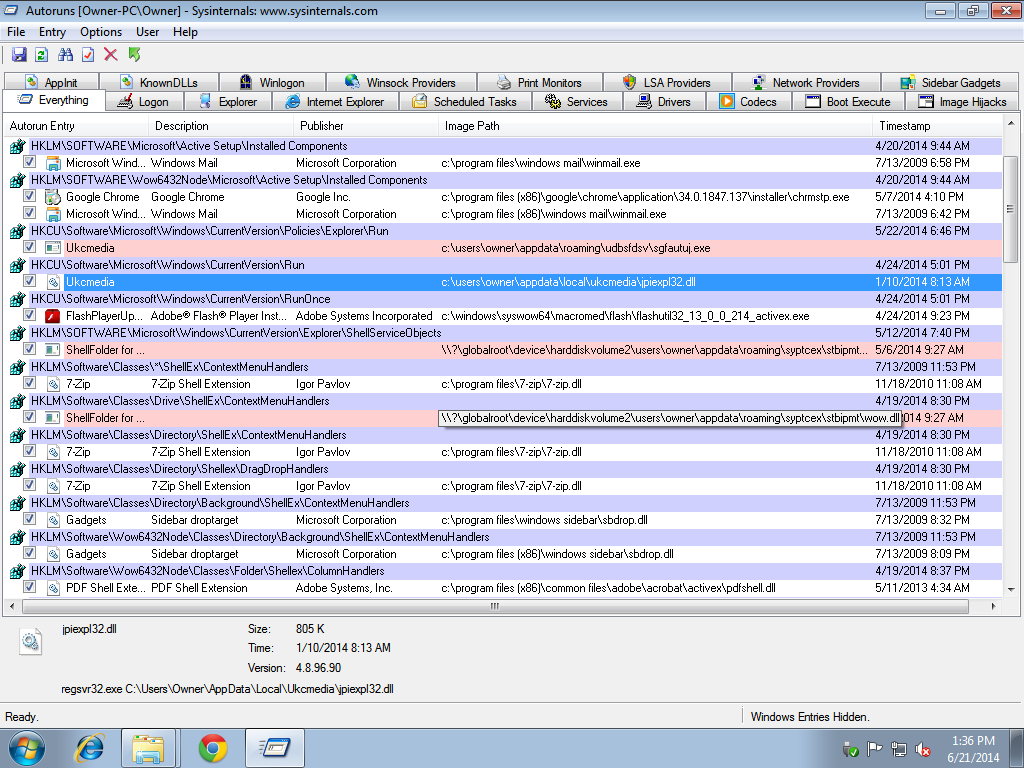
Another Alureon of the new generation (7 if count).
Trojan downloader, works from explorer.exe as first stage and then from zombified svchost.exe.
Contain small x64 loader which only purpose is to launch specified by command line file using syswow64\rundll32.exe
Dropper uses NTFS encryption for own made directory, autorun via HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad as "wow.dll".
Call home in the following format
hello/2.6/101/4434dd11-6b41-4414-8a6d-a9ca7a8e9164/5.1.2600_3.0_32/1/00000000._..o.S.
List of servers
newagelimp.com:80;
newfogfrom.com:80;
95.211.203.99:80;
All strings from dropper
SHA256: 130cdda63e85e616e6f7116dfa73356b9ae02c3e18256165b69a67eec3e036a9
SHA1: 7dc4e3f885797f1e4cd3e0947ecdf34b04533668
MD5: 2d63009761960169773bd1f4c5082a36
https://www.virustotal.com/en/file/130c ... /analysis/
Trojan downloader, works from explorer.exe as first stage and then from zombified svchost.exe.
Contain small x64 loader which only purpose is to launch specified by command line file using syswow64\rundll32.exe
Dropper uses NTFS encryption for own made directory, autorun via HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad as "wow.dll".
Call home in the following format
hello/2.6/101/4434dd11-6b41-4414-8a6d-a9ca7a8e9164/5.1.2600_3.0_32/1/00000000._..o.S.
List of servers
newagelimp.com:80;
newfogfrom.com:80;
95.211.203.99:80;
All strings from dropper
% s % \ s % s IsWow64Process kernel32 shell32.dll \ b a s e n a m e d o b j e c t s \ { % 0 8 x - % 0 4 x - % 0 4 x - % 0 4 x - % 0 4 x % 0 8 x } newagelimp.com:80;newfogfrom.com:80;95.211.203.99:80; j f l s d k j f 0 0 1 . d a t %[^:]:%[^;] 101 2.6 hello %s/%s/%s/%s/%s/%d/%08x google.com %d % S t m p . " % s " 7 " % s " % S W i n S t a 0 \ D e f a u l t GetNativeSystemInfo %d.%d.%d_%d.%d_%d SOFTWARE\Microsoft\Cryptography MachineGuid % s : d e l s o f t w a r e \ c l a s s e s \ c l s i d \ { f b e b 8 a 0 5 - b e e e - 4 4 4 2 - 8 0 4 e - 4 0 9 d 6 c 4 5 1 5 e 9 } \ i n p r o c s e r v e r 3 2 s o f t w a r e \ c l a s s e s \ c l s i d \ { f b e b 8 a 0 5 - b e e e - 4 4 4 2 - 8 0 4 e - 4 0 9 d 6 c 4 5 1 5 e 9 } \ i n p r o c s e r v e r 3 2 s v c h o s t . e x e - k n e t s v c s 6 4 . d l l % w i n d i r % \ s y s t e m 3 2 \ s v c h o s t . e x e - k n e t s v c s s v c h o s t . e x e SHEmptyRecycleBinW r u n d l l 3 2 . e x e % w i n d i r % \ s y s w o w 6 4 \ s v c h o s t . e x e - k n e t s v c s SHQueryRecycleBinW % t e m p % % s \ w o w . d l l r u n d l l 3 2 % s , 0 e x p l o r e r . e x eVT
SHA256: 130cdda63e85e616e6f7116dfa73356b9ae02c3e18256165b69a67eec3e036a9
SHA1: 7dc4e3f885797f1e4cd3e0947ecdf34b04533668
MD5: 2d63009761960169773bd1f4c5082a36
https://www.virustotal.com/en/file/130c ... /analysis/
Attachments
pass: infected
(51.06 KiB) Downloaded 123 times
(51.06 KiB) Downloaded 123 times
Ring0 - the source of inspiration