Packer(or Crypter or Whatever) is changed?After passing the UPX layer , we endup in some piece of code , which is obviously not output of any normal compiler. That binary has additional protection layer we can only assume if generated by builder but most likelly its just crypted with some crypter. Also notice the BitDefenter VersionInfo which is used to stop some Bitdefender signature probably. I seen this version info at more malware samples.
A forum for reverse engineering, OS internals and malware analysis
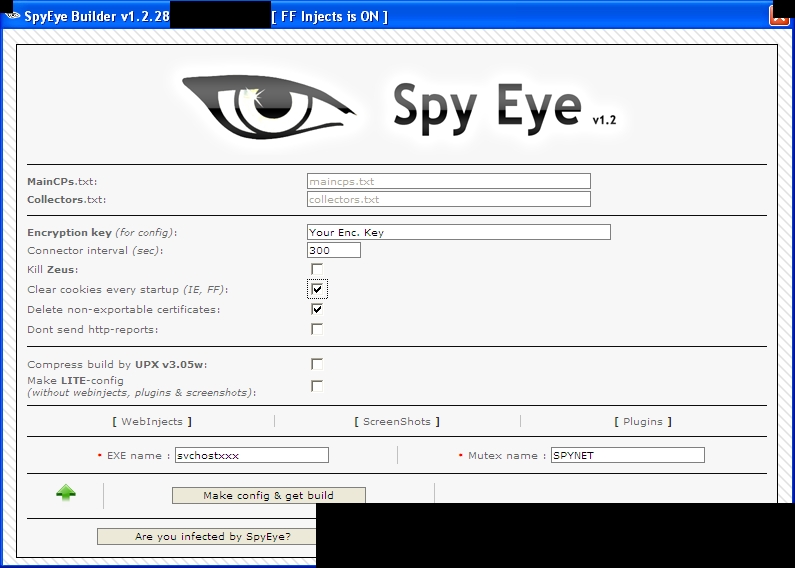
Screenshot of SpyEye 1.2.28 builder.
Another public directory.
hxxp://mydocumentsnew.com/main/bin/
Another public directory.
hxxp://mydocumentsnew.com/main/bin/
Attachments
I meant to post this awhile ago but forgot.
SpyEye analysis
- http://www.malwareint.com/docs/spyeye-analysis-en.pdf
- http://www.malwareint.com/docs/spyeye-a ... -ii-en.pdf
SpyEye analysis
- http://www.malwareint.com/docs/spyeye-analysis-en.pdf
- http://www.malwareint.com/docs/spyeye-a ... -ii-en.pdf
Who controls the past controls the future
Who controls the present controls the past
Who controls the present controls the past
Public directory
200.56.243.137/joomla/administrator/bin/
All data in attach.
http://www.virustotal.com/file-scan/rep ... 1285947131
http://www.virustotal.com/file-scan/rep ... 1285947138
http://www.virustotal.com/file-scan/rep ... 1285947153
200.56.243.137/joomla/administrator/bin/
All data in attach.
http://www.virustotal.com/file-scan/rep ... 1285947131
http://www.virustotal.com/file-scan/rep ... 1285947138
http://www.virustotal.com/file-scan/rep ... 1285947153
Attachments
pass: malware
(1.23 MiB) Downloaded 79 times
(1.23 MiB) Downloaded 79 times
Ring0 - the source of inspiration
could be a new version, found it on infected pc.
http://www.virustotal.com/file-scan/rep ... 1286479854
http://www.virustotal.com/file-scan/rep ... 1286479854
Attachments
(233.94 KiB) Downloaded 79 times
The above sample SHA1 : ddedb2cb0a67421a70bcf71deaaec304d79b1c7f - whatever it is.
Start:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"fheydbueyj.exe"="C:\\fheydbueyj.exe\\fheydbueyj.exe"
Files:
C:\fheydbueyj.exe\fheydbueyj.exe
C:\fheydbueyj.exe\config.bin
c:\documents and settings\NetworkService\Local Settings\Application Data\DBControl
c:\documents and settings\LocalService\Local Settings\Application Data\DBControl
C:\DBControl
C:\documents and settings\CurrentUser\Local Settings\Application Data\DBControl
Hooks every process that it can:
ntdll.dll-->NtEnumerateValueKey, Type: Inline - RelativeJump 0x7C90D2EE-->00000000 [unknown_code_page]
ntdll.dll-->NtQueryDirectoryFile, Type: Inline - RelativeJump 0x7C90D76E-->00000000 [unknown_code_page]
ntdll.dll-->NtResumeThread, Type: Inline - RelativeJump 0x7C90DB3E-->00000000 [unknown_code_page]
ntdll.dll-->NtVdmControl, Type: Inline - RelativeJump 0x7C90DF1E-->00000000 [unknown_code_page]
ntdll.dll-->LdrLoadDll, Type: Inline - RelativeJump 0x7C9163C3-->00000000 [unknown_code_page]
advapi32.dll-->CryptEncrypt, Type: Inline - RelativeJump 0x77DEE360-->00000000 [unknown_code_page]
user32.dll-->TranslateMessage, Type: Inline - RelativeJump 0x7E418BF6-->00000000 [unknown_code_page]
wininet.dll-->InternetReadFile, Type: Inline - RelativeJump 0x3D94654B-->00000000 [unknown_code_page]
wininet.dll-->HttpQueryInfoA, Type: Inline - RelativeJump 0x3D94878D-->00000000 [unknown_code_page]
wininet.dll-->InternetCloseHandle, Type: Inline - RelativeJump 0x3D949088-->00000000 [unknown_code_page]
wininet.dll-->InternetQueryDataAvailable, Type: Inline - RelativeJump 0x3D94BF7F-->00000000 [unknown_code_page]
wininet.dll-->HttpAddRequestHeadersA, Type: Inline - RelativeJump 0x3D94CF46-->00000000 [unknown_code_page]
wininet.dll-->HttpOpenRequestA, Type: Inline - RelativeJump 0x3D94D508-->00000000 [unknown_code_page]
wininet.dll-->HttpSendRequestW, Type: Inline - RelativeJump 0x3D94FABE-->00000000 [unknown_code_page]
wininet.dll-->HttpSendRequestA, Type: Inline - RelativeJump 0x3D95EE89-->00000000 [unknown_code_page]
wininet.dll-->InternetReadFileExA, Type: Inline - RelativeJump 0x3D963381-->00000000 [unknown_code_page]
wininet.dll-->InternetWriteFile, Type: Inline - RelativeJump 0x3D9A60F6-->00000000 [unknown_code_page]
ws2_32.dll-->send, Type: Inline - RelativeJump 0x71AB4C27-->00000000 [unknown_code_page]
Start:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"fheydbueyj.exe"="C:\\fheydbueyj.exe\\fheydbueyj.exe"
Files:
C:\fheydbueyj.exe\fheydbueyj.exe
C:\fheydbueyj.exe\config.bin
c:\documents and settings\NetworkService\Local Settings\Application Data\DBControl
c:\documents and settings\LocalService\Local Settings\Application Data\DBControl
C:\DBControl
C:\documents and settings\CurrentUser\Local Settings\Application Data\DBControl
Hooks every process that it can:
ntdll.dll-->NtEnumerateValueKey, Type: Inline - RelativeJump 0x7C90D2EE-->00000000 [unknown_code_page]
ntdll.dll-->NtQueryDirectoryFile, Type: Inline - RelativeJump 0x7C90D76E-->00000000 [unknown_code_page]
ntdll.dll-->NtResumeThread, Type: Inline - RelativeJump 0x7C90DB3E-->00000000 [unknown_code_page]
ntdll.dll-->NtVdmControl, Type: Inline - RelativeJump 0x7C90DF1E-->00000000 [unknown_code_page]
ntdll.dll-->LdrLoadDll, Type: Inline - RelativeJump 0x7C9163C3-->00000000 [unknown_code_page]
advapi32.dll-->CryptEncrypt, Type: Inline - RelativeJump 0x77DEE360-->00000000 [unknown_code_page]
user32.dll-->TranslateMessage, Type: Inline - RelativeJump 0x7E418BF6-->00000000 [unknown_code_page]
wininet.dll-->InternetReadFile, Type: Inline - RelativeJump 0x3D94654B-->00000000 [unknown_code_page]
wininet.dll-->HttpQueryInfoA, Type: Inline - RelativeJump 0x3D94878D-->00000000 [unknown_code_page]
wininet.dll-->InternetCloseHandle, Type: Inline - RelativeJump 0x3D949088-->00000000 [unknown_code_page]
wininet.dll-->InternetQueryDataAvailable, Type: Inline - RelativeJump 0x3D94BF7F-->00000000 [unknown_code_page]
wininet.dll-->HttpAddRequestHeadersA, Type: Inline - RelativeJump 0x3D94CF46-->00000000 [unknown_code_page]
wininet.dll-->HttpOpenRequestA, Type: Inline - RelativeJump 0x3D94D508-->00000000 [unknown_code_page]
wininet.dll-->HttpSendRequestW, Type: Inline - RelativeJump 0x3D94FABE-->00000000 [unknown_code_page]
wininet.dll-->HttpSendRequestA, Type: Inline - RelativeJump 0x3D95EE89-->00000000 [unknown_code_page]
wininet.dll-->InternetReadFileExA, Type: Inline - RelativeJump 0x3D963381-->00000000 [unknown_code_page]
wininet.dll-->InternetWriteFile, Type: Inline - RelativeJump 0x3D9A60F6-->00000000 [unknown_code_page]
ws2_32.dll-->send, Type: Inline - RelativeJump 0x71AB4C27-->00000000 [unknown_code_page]
Attachments
(318.88 KiB) Downloaded 73 times
Attachments
(252.27 KiB) Downloaded 73 times
SpyEye v1.2.x
http://www.virustotal.com/file-scan/rep ... 1287599762
unpacked dropper attached.
http://www.virustotal.com/file-scan/rep ... 1287599762
unpacked dropper attached.
skype Skype msnmsgr %s!%s!%08X ! %08X Software\Microsoft\Internet Explorer Version User Admin ONLINE md5= ccrc= cpu= plg= rep= tid= ut= os= ie= stat= ver= & guid= ? PLUGIN LOAD-COMPLETE LOAD-ERROR ACTIVE LOAD UPDATE_CONFIG PATH UPDATE <br> SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN %s%s\%s %s\ntdll.dll __SPYNET_RELOADCFG__ __SPYNET_UNINSTALL__ \\.\pipe\globpluginsuninstallpipe TASK IS OK [ERROR] : CreateProcess("%s", ..., "%s") fails : dwFileSize == 0x%08X; dwCrc32 == 0x%08X : dwErr == %d [ERROR] : DumpPage("%s", "%s") fails : dwErr == %d upd [ERROR] : Empty szLink? : dwErr == %d [ERROR] : Empty data? : dwErr == %d [ERROR] : Empty report. Unknown error : dwErr == %d [ERROR] : Thread is really sloppy : dwErr == %d [ERROR] : Cannot create thread. 0o : dwErr == %d .. \*.* collectors.txt maincps.txt ; .cfg .dll
anonymous xWS2send GRABBED DATA %s%s%s EMPTY Content-Type: .accdb .ppsx .pps .docx .doc .xlsx .xls .xml .txt .pdf .7z .rar .zip .exe .ico .mpeg .mpg .avi .mng .flv .bmp .swf .gif .png .jpeg .jpg .css .js Accept-Encoding: SOFTWARE\Microsoft\Internet Explorer Connection: close
Keep-Alive: Keep-Alive: Connection: keep-alive HTTP/1. Content-Length: %u Cteonnt-Length: Content-Length: l script text/ Content-Length Content-Type Connection: close
Connection: Content-Encoding: deflate gzip Transfer-Encoding: chunked data_end data_after data_inject data_before set_url gp * g p %x \ \ B a s e N a m e d O b j e c t s \ \ \ . \ p i p e \ _AVIRA_ __SYSTEM__ 1.2.4
Attachments
pass: malware
(78.87 KiB) Downloaded 83 times
(78.87 KiB) Downloaded 83 times
Ring0 - the source of inspiration
SpyEye Builder 1.1.39 together with an Anti Hardware ID (hwid) patch was leaked.
And BTW there are siome opinions about merging SpyEye and ZBot.
And BTW there are siome opinions about merging SpyEye and ZBot.