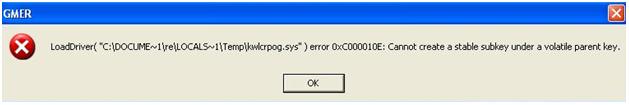
New installer for FakeSysDef, hope this installs the new rootkit!
Attachments
pass:malware
(433.36 KiB) Downloaded 54 times
(433.36 KiB) Downloaded 54 times
A forum for reverse engineering, OS internals and malware analysis
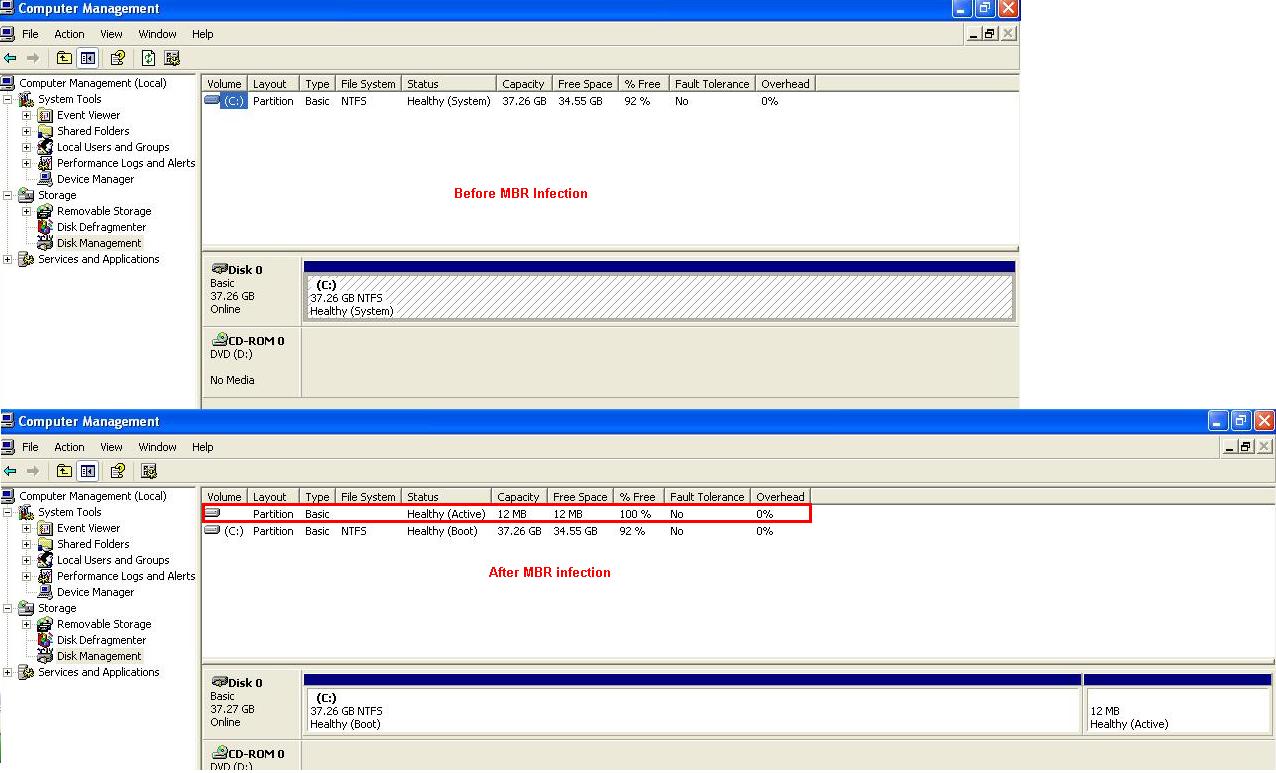
In Gmer except Services, Registry and Files other options are disabled