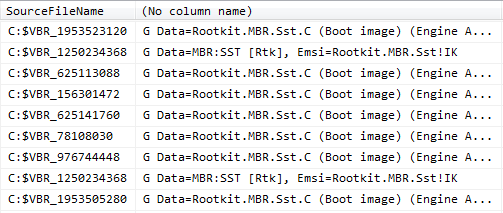
NarfBang wrote:Hey all,afair, dates of course not 100% correct
Does anyone have a family tree of TDSS and its progeny?
I'm interested in the timelines and history of how this family is evolving.
Cheers if ya want to move this post to a different thread.
TDSS (TDL1), May-July 2008
TDL2 Apr-May 2009, gets generally updated twice
Pragma TDL2 mods from summer 2009, till maybe the fall of 2010
TDL3 end of Aug, Sept 2009, gets update after 2 months, then updates every months until end of April 2010.
z00clicker split of TDL3 - somewhere in the end-beginning of 2010
TDL4 - end of July 2010, gets update in Aug and Sept of the same year.
MaxSS (Pragma TDL3 mod) - end-beginning of 2011
MaxSS (Pragma TDL4 mod) - somewhere in the beginning of summer 2011, some sort of test launch
MaxSS (Pragma TDL4 mod + VBR) - Aug 2011, updated in October
Ring0 - the source of inspiration