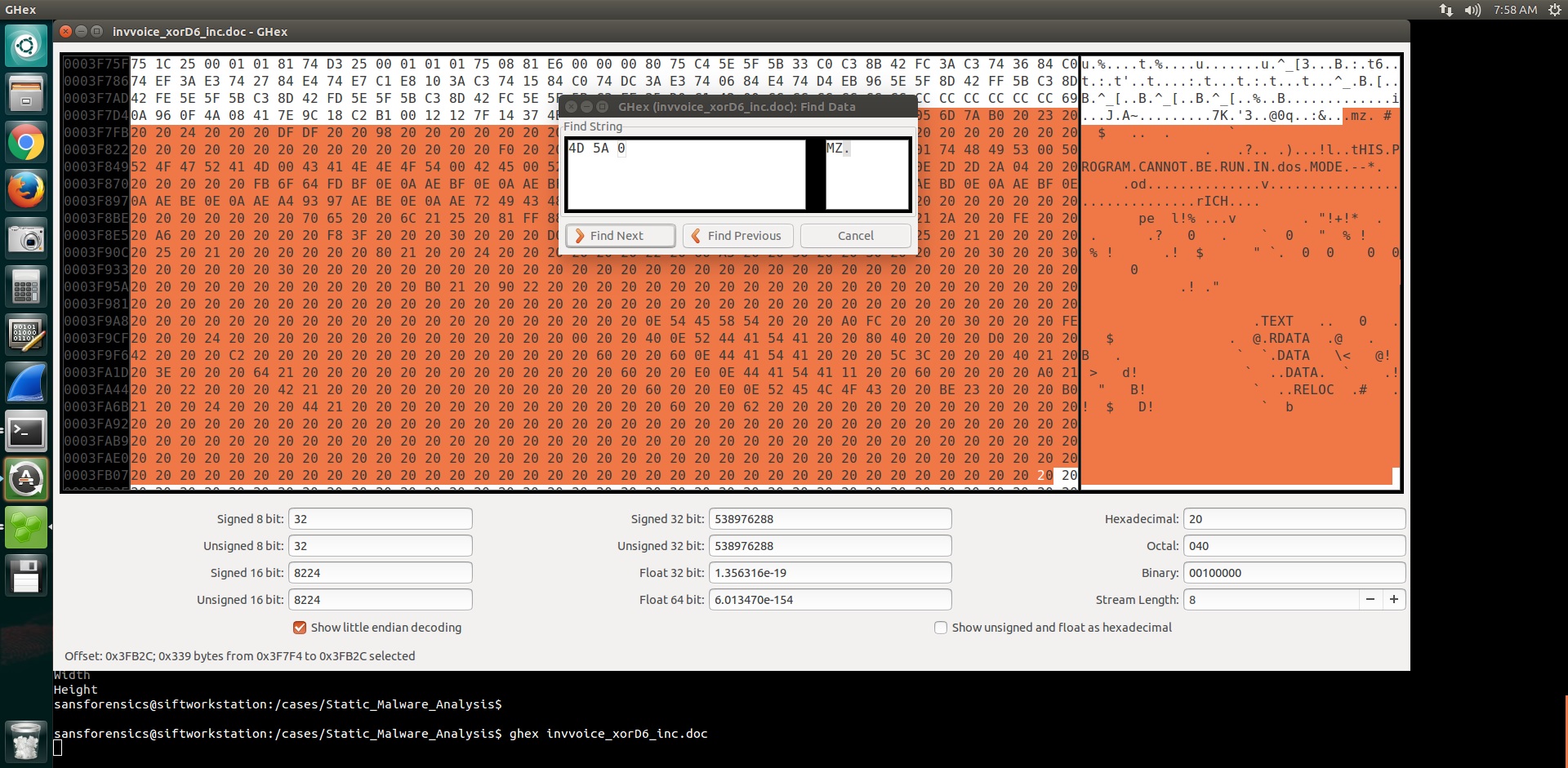
This malware same is already been analyzed, but I tried working it on my own as an exercise, so I ran bbcrack.py against it and got it decoded. I see an MZ header in there indicating an embedded executable in the Word document.
https://malwr.com/analysis/NTEzMjYxZDE0 ... RjZTRkNDQ/
I can see this analysis says there is a connection going out to 91.239.232.145
I was hoping to be able to find that IP address or its corresponding URL during my analysis, but nothing.
I ran Foremost against the bbcrack deobfuscated file (xorD6 + inc) hoping it would pull out the executable so I could drill into that, but all Foremost pulled out was another embedded Word doc.
Just trying to figure out where that IP is hidden and why Foremost isnt carving out the .exe for me.
https://malwr.com/analysis/NTEzMjYxZDE0 ... RjZTRkNDQ/
I can see this analysis says there is a connection going out to 91.239.232.145
I was hoping to be able to find that IP address or its corresponding URL during my analysis, but nothing.
I ran Foremost against the bbcrack deobfuscated file (xorD6 + inc) hoping it would pull out the executable so I could drill into that, but all Foremost pulled out was another embedded Word doc.
Just trying to figure out where that IP is hidden and why Foremost isnt carving out the .exe for me.