MSM standart BS
Actual report, additionally copy of it attached here for comedy section purposes
https://www.cymmetria.com/wp-content/up ... chwork.pdf
Key features of story:
1) Unknown startup pseudo-security company with stuff similar to SentinelOne
2) Newly "discovered" APT (Advanced Packaging Tool?)
3) Malware itself massive copy-paste from various github projects, blogs
4) Mentally unbalanced Cymmetria staff, who seems little upset and disappointed
1) Cymmetria - "security" startup unknown before end of 2014.
Their products - typical bullshit
https://www.cymmetria.com/product/
Compare to SentinelOne
https://sentinelone.com/products/
Btw they share the not only trashing design but the same registar, in only difference SentinelOne started it's "operations" in 2013, and this one in 2014.
And when I looked on their company stuff, pff, so that's expains everything.
Co-founder:
2) So what about this advanced packaging tool (I hope it is really this, not Advanced Persistent Threat).
This bundle of various combined shits is in attach. Most interesting part of it huge initial dropper which is AutoIt script converted to exe (feeling how advanced/elite this already?).
The only ONE thing that attached my attention to this "campaign" and this crap was declared usage of my tool inside of it.
Some master class for "elite" "cybersecurity" : there is no method called this name. It doesn't exist.
Itself this malware not interesting at all, so skip and go to 3. But who interested here is the full story: AutoIT, Meterpreter, public sploits, UACME, PowerShell and Google search. Sounds so interesting! (no it is not)
3) Param Pam Pam.
Meet UACME usage in this "APT".
So I dumped it from AutoIt trash and looked on it.
http://www.labofapenetrationtester.com/ ... shell.html
Full copy-paste of this article. FULL even filenames and content of injector dll.
Authors were so dumb, so they even don't understand how it actually work. Instead of using execution parameter they implemented startup of batch file. Facepalm. And to Cymmetria too.
Makecab to make cab(lol) with injector dll and drop it to system32\oobe as wdscore.dll (Yes you are right! This is Win32/Carberp (wusa) & WinNT/Pitou (SETUPSQM.EXE + wdscore) method. Not "UACME method"). Not to mention UACME is actually don't use makecab and packs file by itself. But who am I and who are these "elite" "cybersecuirty" veterans.
It is very interesting that so-called "elite" "cybersecurity" experts doesn't know how popular malware families work, what they use, how they install and what exploit. Must be too much complicated to use google.
This dll is Fubuki injector from UACME v1.9. But how they found its from UACME? By version info I left in every dll. Praise the skid who build package they didn't removed it otherwise these "elite" would have decided that this is some kind of 0day (remember Google is banned and Carberp/Pitou are unknown words for Cymmetria).
Lets get back to their paper.
Next, some heavy drugs delivered to Cymmetria office (hint: IFileOperation from MS binary VA).
4) Initially, because of low quality article and unknown publisher I thought they are speaking about small dll they mention in list of files. So I removed UPX from it (wow sophisticated APT packer) and did F5 in IDA, figured out this is just another IFileOperation dll (copying one file) and posted about it. Despite the obvious error, second part of my post was absolutely correct and I repost and repost it again.
For my surprise some angry Cymmetria guy poped up, demonstrating how he upset and disapointed (like if would I care about this, really).
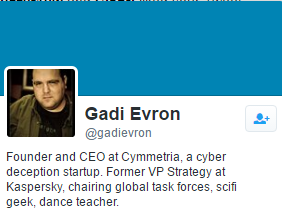
Meet the hero. A former Kaspersky employee. I've a long story with Kaspersky AV and their staff (hello Gostev) and I will remember you too, "dance teacher" (яйца то не мешают?) :)
<- highly recommend to follow, for further "APTs".
TL;DR
Meet the script-kiddie malware bundle mislabeled as "APT", build by script-kiddies and researched by script-kiddies "elite" "cybersecurity" clowns veterans.
P.S.
Dear Cymmetria clowns please remove all references to my project from your shit "article". I don't want to have anything in common with a pseudo-security firm full of "dalbaebs".
New "Patchwork" Cyber-Espionage Group Uses Copy-Pasted Malware for Its Attackshttp://news.softpedia.com/news/new-patc ... 6101.shtml
Actual report, additionally copy of it attached here for comedy section purposes
https://www.cymmetria.com/wp-content/up ... chwork.pdf
Key features of story:
1) Unknown startup pseudo-security company with stuff similar to SentinelOne
2) Newly "discovered" APT (Advanced Packaging Tool?)
3) Malware itself massive copy-paste from various github projects, blogs
4) Mentally unbalanced Cymmetria staff, who seems little upset and disappointed
1) Cymmetria - "security" startup unknown before end of 2014.
Their products - typical bullshit
https://www.cymmetria.com/product/
Compare to SentinelOne
https://sentinelone.com/products/
Btw they share the not only trashing design but the same registar, in only difference SentinelOne started it's "operations" in 2013, and this one in 2014.
And when I looked on their company stuff, pff, so that's expains everything.
Co-founder:
Former Officer of an elite cyber unit within Unit 8200 (Israel Defense Forces).Co-founder 2:
Veteran of Israel Defense Forces (IDF) Unit 8200, where he led advanced security research as Captain of an elite cyber R&D team.CEO
· 15 years of experience in the field of cybersecurity.Lets compare it to SentinelOne (they may have nothing common in reality, but everything in details).
· Former VP Cybersecurity Strategy at Kaspersky Lab and Head of PwC’s Cyber Security Center of Excellence.
SentinelOne was founded in 2013 by an elite group of Israeli cybersecurity experts who developed a fundamentally new, groundbreaking approach to endpoint protection capable of defeating the most advanced malware, exploits and cyber attacks.Here and there we have "elite" "cybersecurity" experts from Israel. Okay, you are elite, I don't mind.
2) So what about this advanced packaging tool (I hope it is really this, not Advanced Persistent Threat).
This bundle of various combined shits is in attach. Most interesting part of it huge initial dropper which is AutoIt script converted to exe (feeling how advanced/elite this already?).
The only ONE thing that attached my attention to this "campaign" and this crap was declared usage of my tool inside of it.
This script then bypassed UAC using a known method called UACME"Method called UACME"? Lol what?
Some master class for "elite" "cybersecurity" : there is no method called this name. It doesn't exist.
Itself this malware not interesting at all, so skip and go to 3. But who interested here is the full story: AutoIT, Meterpreter, public sploits, UACME, PowerShell and Google search. Sounds so interesting! (no it is not)
3) Param Pam Pam.
Meet UACME usage in this "APT".
So I dumped it from AutoIt trash and looked on it.
http://www.labofapenetrationtester.com/ ... shell.html
Full copy-paste of this article. FULL even filenames and content of injector dll.
Authors were so dumb, so they even don't understand how it actually work. Instead of using execution parameter they implemented startup of batch file. Facepalm. And to Cymmetria too.
Makecab to make cab(lol) with injector dll and drop it to system32\oobe as wdscore.dll (Yes you are right! This is Win32/Carberp (wusa) & WinNT/Pitou (SETUPSQM.EXE + wdscore) method. Not "UACME method"). Not to mention UACME is actually don't use makecab and packs file by itself. But who am I and who are these "elite" "cybersecuirty" veterans.
It is very interesting that so-called "elite" "cybersecurity" experts doesn't know how popular malware families work, what they use, how they install and what exploit. Must be too much complicated to use google.
This dll is Fubuki injector from UACME v1.9. But how they found its from UACME? By version info I left in every dll. Praise the skid who build package they didn't removed it otherwise these "elite" would have decided that this is some kind of 0day (remember Google is banned and Carberp/Pitou are unknown words for Cymmetria).
Lets get back to their paper.
After the previous stages, the payload uses a well known and as-of-yet unpatched UAC bypassMeet another bullshit. Microsoft didn't patched it everywhere, because "UAC is not a security boundary" (I'm so happy I can say this). But MS take care about it. It doesn't work on Windows 10 (which is a FREE upgrage of Windows 7, offer end july 2016) because oobe is redesigned and target application does not exist.
vulnerability in Microsoft Windows (known as UACME8), which works on the default setup of
Windows 7.
Next, some heavy drugs delivered to Cymmetria office (hint: IFileOperation from MS binary VA).
the payload hides the UAC bypassI read this 5 or maybe 7 times to understand what they mean. They are really elite.
vulnerability exploitation inside svchost.exe using a technique called Process Hollowing10 (UAC bypass method – ‘IFileOperation COM Object’11)
4) Initially, because of low quality article and unknown publisher I thought they are speaking about small dll they mention in list of files. So I removed UPX from it (wow sophisticated APT packer) and did F5 in IDA, figured out this is just another IFileOperation dll (copying one file) and posted about it. Despite the obvious error, second part of my post was absolutely correct and I repost and repost it again.
For my surprise some angry Cymmetria guy poped up, demonstrating how he upset and disapointed (like if would I care about this, really).
Meet the hero. A former Kaspersky employee. I've a long story with Kaspersky AV and their staff (hello Gostev) and I will remember you too, "dance teacher" (яйца то не мешают?) :)
<- highly recommend to follow, for further "APTs".
TL;DR
Meet the script-kiddie malware bundle mislabeled as "APT", build by script-kiddies and researched by script-kiddies "elite" "cybersecurity" clowns veterans.
P.S.
Dear Cymmetria clowns please remove all references to my project from your shit "article". I don't want to have anything in common with a pseudo-security firm full of "dalbaebs".
Attachments
pass: infected
(2.15 MiB) Downloaded 105 times
(2.15 MiB) Downloaded 105 times
pass: infected
(1.82 MiB) Downloaded 103 times
(1.82 MiB) Downloaded 103 times
Ring0 - the source of inspiration