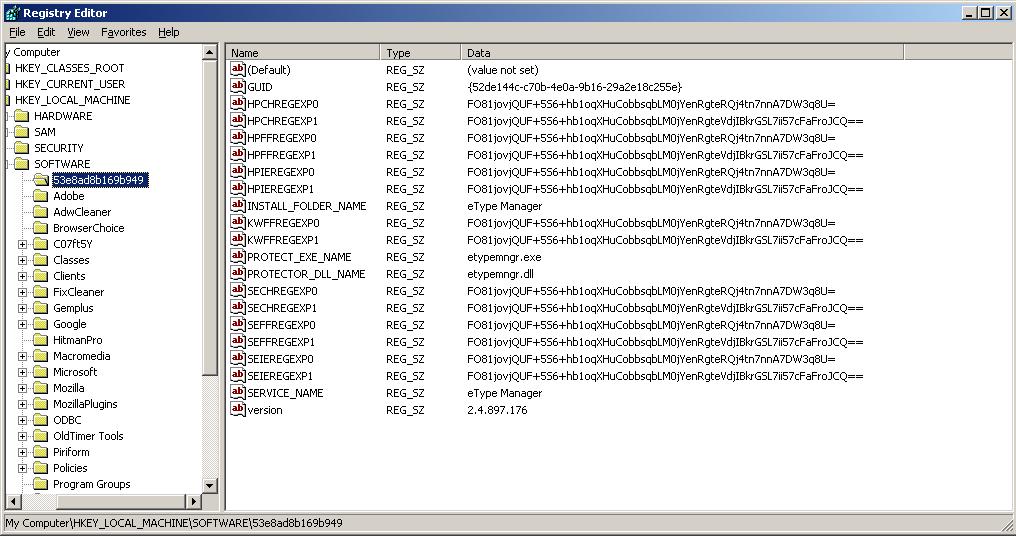
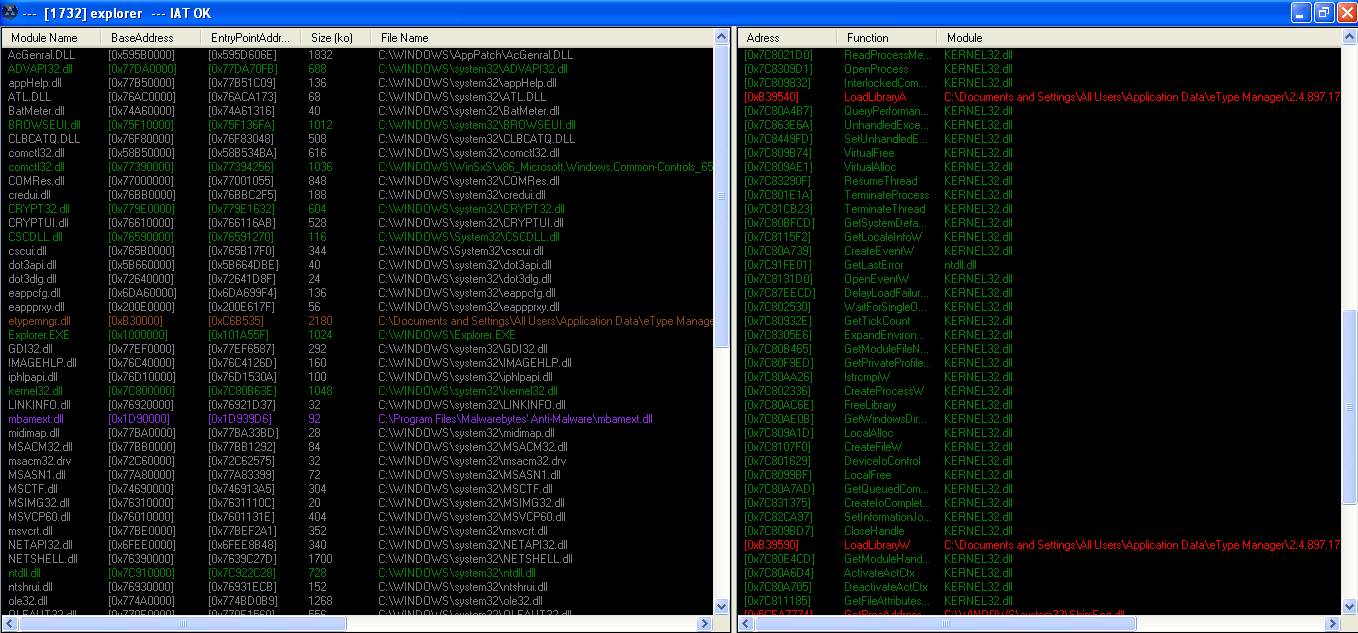
It uses HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\Appinit_Dlls. Multiple IAT hooks in every process where this dll loaded. Including hooks to protect own registry entry, files so it sort of primitive user mode rootkit.
Code: Select all[1192]explorer.exe-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x010011D4-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x01001254-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtCreateFile, Type: IAT Modification 0x7C801008-->022B9770 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtOpenFile, Type: IAT Modification 0x7C801014-->022B9700 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtQueryInformationFile, Type: IAT Modification 0x7C801018-->022B90A0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtSetInformationFile, Type: IAT Modification 0x7C801030-->022B98B0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtClose, Type: IAT Modification 0x7C80103C-->022BC1D0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtQueryValueKey, Type: IAT Modification 0x7C801058-->022BBFC0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtOpenKey, Type: IAT Modification 0x7C80105C-->022BC110 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtSetValueKey, Type: IAT Modification 0x7C801064-->022BC030 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtCreateKey, Type: IAT Modification 0x7C801068-->022BC0A0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtEnumerateKey, Type: IAT Modification 0x7C8010E8-->022BBEE0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtEnumerateValueKey, Type: IAT Modification 0x7C801194-->022BBF50 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtReadFile, Type: IAT Modification 0x7C80119C-->022B9080 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtWriteFile, Type: IAT Modification 0x7C8011BC-->022B97F0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtQueryKey, Type: IAT Modification 0x7C8011D0-->022B9060 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtDeleteValueKey, Type: IAT Modification 0x7C8011D4-->022BC2A0 [etypemngr.dl]
[1192]explorer.exe-->kernel32.dll-->ntdll.dll-->NtFlushBuffersFile, Type: IAT Modification 0x7C801240-->022B9420 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x77DC11E0-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x77DC1214-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtQueryKey, Type: IAT Modification 0x77DC125C-->022B9060 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtEnumerateKey, Type: IAT Modification 0x77DC1274-->022BBEE0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtQueryInformationFile, Type: IAT Modification 0x77DC12B0-->022B90A0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtCreateFile, Type: IAT Modification 0x77DC12F0-->022B9770 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtWriteFile, Type: IAT Modification 0x77DC12F8-->022B97F0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtReadFile, Type: IAT Modification 0x77DC130C-->022B9080 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtFlushBuffersFile, Type: IAT Modification 0x77DC1310-->022B9420 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtSetInformationFile, Type: IAT Modification 0x77DC1314-->022B98B0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtDeleteValueKey, Type: IAT Modification 0x77DC1344-->022BC2A0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtEnumerateValueKey, Type: IAT Modification 0x77DC1348-->022BBF50 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtDeleteKey, Type: IAT Modification 0x77DC1424-->022BC250 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtQueryValueKey, Type: IAT Modification 0x77DC1428-->022BBFC0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtSetValueKey, Type: IAT Modification 0x77DC142C-->022BC030 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtOpenKey, Type: IAT Modification 0x77DC1448-->022BC110 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtCreateKey, Type: IAT Modification 0x77DC144C-->022BC0A0 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtOpenFile, Type: IAT Modification 0x77DC148C-->022B9700 [etypemngr.dl]
[1192]explorer.exe-->advapi32.dll-->ntdll.dll-->NtClose, Type: IAT Modification 0x77DC1494-->022BC1D0 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x7E3612F4-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x7E361340-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtQueryKey, Type: IAT Modification 0x7E3613F4-->022B9060 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtEnumerateValueKey, Type: IAT Modification 0x7E3613F8-->022BBF50 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtCreateKey, Type: IAT Modification 0x7E361454-->022BC0A0 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtSetValueKey, Type: IAT Modification 0x7E361458-->022BC030 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtDeleteValueKey, Type: IAT Modification 0x7E36145C-->022BC2A0 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtEnumerateKey, Type: IAT Modification 0x7E3614C8-->022BBEE0 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtOpenKey, Type: IAT Modification 0x7E3614CC-->022BC110 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtClose, Type: IAT Modification 0x7E3614D0-->022BC1D0 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->ntdll.dll-->NtQueryValueKey, Type: IAT Modification 0x7E3614D4-->022BBFC0 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x77F11084-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x77F110B8-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->ntdll.dll-->NtOpenFile, Type: IAT Modification 0x77F11154-->022B9700 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->ntdll.dll-->NtQueryInformationFile, Type: IAT Modification 0x77F11158-->022B90A0 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->ntdll.dll-->NtOpenKey, Type: IAT Modification 0x77F11194-->022BC110 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->ntdll.dll-->NtQueryValueKey, Type: IAT Modification 0x77F11198-->022BBFC0 [etypemngr.dl]
[1192]explorer.exe-->gdi32.dll-->ntdll.dll-->NtClose, Type: IAT Modification 0x77F1119C-->022BC1D0 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x7C9C13E8-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x7C9C15A0-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtCreateFile, Type: IAT Modification 0x7C9C16DC-->022B9770 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtEnumerateValueKey, Type: IAT Modification 0x7C9C16F4-->022BBF50 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtOpenKey, Type: IAT Modification 0x7C9C16F8-->022BC110 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtOpenFile, Type: IAT Modification 0x7C9C1724-->022B9700 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtQueryInformationFile, Type: IAT Modification 0x7C9C172C-->022B90A0 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtClose, Type: IAT Modification 0x7C9C1730-->022BC1D0 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->ntdll.dll-->NtSetInformationFile, Type: IAT Modification 0x7C9C1734-->022B98B0 [etypemngr.dl]
[1192]explorer.exe-->shell32.dll-->user32.dll-->SetWindowsHookExW, Type: IAT Modification 0x7C9C20F0-->022B94E0 [etypemngr.dl]
[1192]explorer.exe-->wininet.dll-->kernel32.dll-->LoadLibraryW, Type: IAT Modification 0x771A122C-->022B9590 [etypemngr.dl]
[1192]explorer.exe-->wininet.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x771A1250-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->ws2_32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x71A910A8-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT Modification 0x77A71190-->022B9540 [etypemngr.dl]
[1192]explorer.exe-->user32.dll-->DialogBoxParamW, Type: Inline - RelativeJump 0x7E3747AB-->022B4430 [etypemngr.dl]
It doesn't check their integrity however, once they are removed it is possible to remove reg entry. The direct syscalls also will work.
This dll can't be unloaded until these hooks are in place, otherwise application will crash. So I think reboot is required.