This ransomware encrypts user data with AES, and then requires a 300$ repurchase to BTC to return the files. In a week the amount is doubled.
#DECRYPT_MY_FILES#.txt - text note
#DECRYPT_MY_FILES#.html - web page
#DECRYPT_MY_FILES.BMP - desktop wallpaller
#DECRYPT_MY_FILES#.vbs - script for the audio message
Text note:

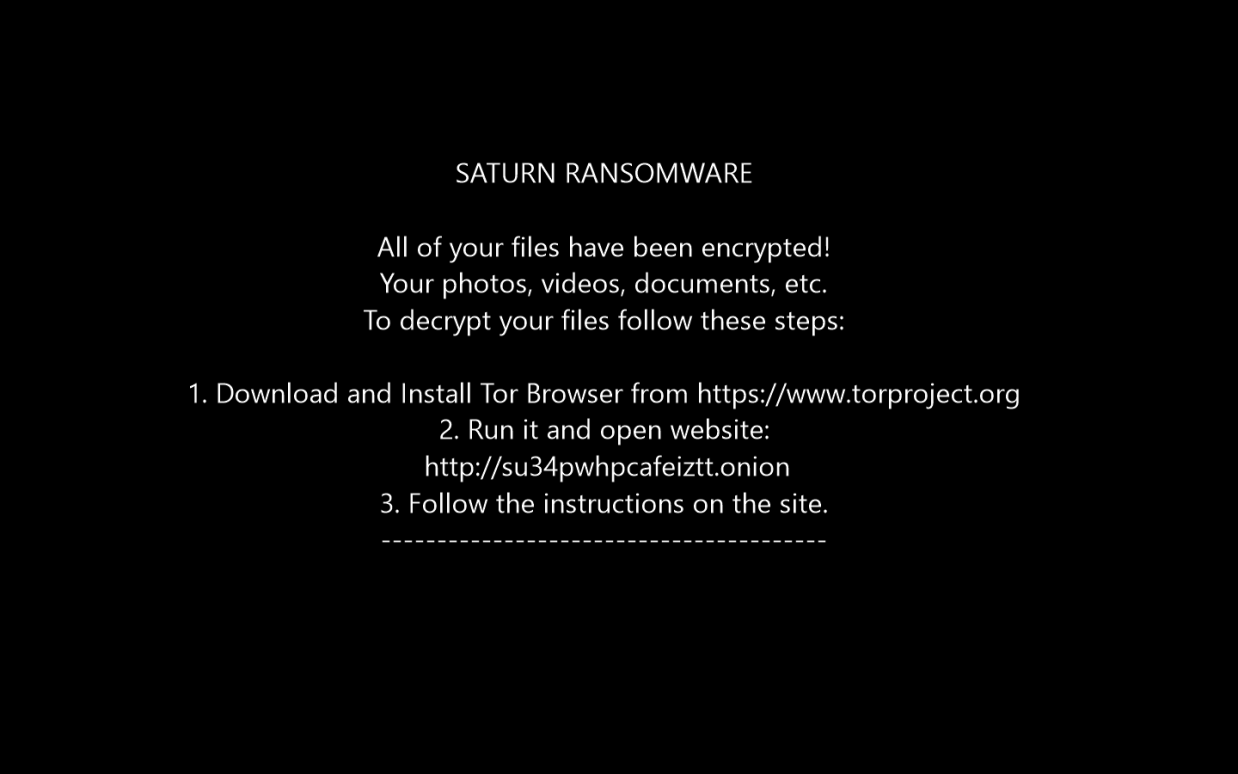
Web page:

Desktop wallpaller:
Script for the audio message:

Screenshots of the pages of "Tor" extortion site:



Deletes shadow copies of files, disables Windows recovery and repair functions at the download stage with the command:
#DECRYPT_MY_FILES#.txt - text note
#DECRYPT_MY_FILES#.html - web page
#DECRYPT_MY_FILES.BMP - desktop wallpaller
#DECRYPT_MY_FILES#.vbs - script for the audio message
Text note:

Web page:

Desktop wallpaller:
Script for the audio message:

Screenshots of the pages of "Tor" extortion site:



Deletes shadow copies of files, disables Windows recovery and repair functions at the download stage with the command:
Code: Select all
List of file extensions to be encrypted:
cmd.exe /C vssadmin.exe delete shadows /all /quiet & wmic.exe shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quietCode: Select all
VT: https://www.virustotal.com/en/file/9e87 ... 518702835/.123, .1cd, .3dm, .3ds, .602, .accdb, .aif, .apk, .asm, .asp, .avi, .backup, .bak, .bat, .bmp, .cdr, .cfg, .cgm, .class, .com, .config, .cpp, .crt, .csr, .csv, .dat, .dbf, .dif, .doc, .docm, .docp, .docx, .dwg, .gadget, .gif, .h, .ico, .iff, .jar, .java, .jpeg, .jpg, .json, .lib, .m3u, .m4a, .max, .mdb, .mid, .mov, .mp3, .mp4, .mpa, .ms11 .(Security .copy), .ms11, .msg, .nef, .obj, .odg, .odt, .ogg, .p12, .pages, .pas, .pdb, .pdf, .pem, .php, .png, .pproj, .pps, .ppt, .pptm, .pptx, .prproj, .ps1, .psd, .py, .qcow2, .rar, .rtf, .sfk, .sql, .sqlite, .svg, .tar, .text, .tif, .tiff, .torrent, .txt, .vbox, .vbs, .vdi, .veg, .vmdk, .vmx, .wallet, .wav, .wma, .wmv, .wpd, .wps, .wsf, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xml, .zipAttachments
(182.68 KiB) Downloaded 86 times