I'm trying to examine a computer with a possible rootkit onboard. The user had removed two rootkits (?) called Rloader.a and Rloader.b some time ago.
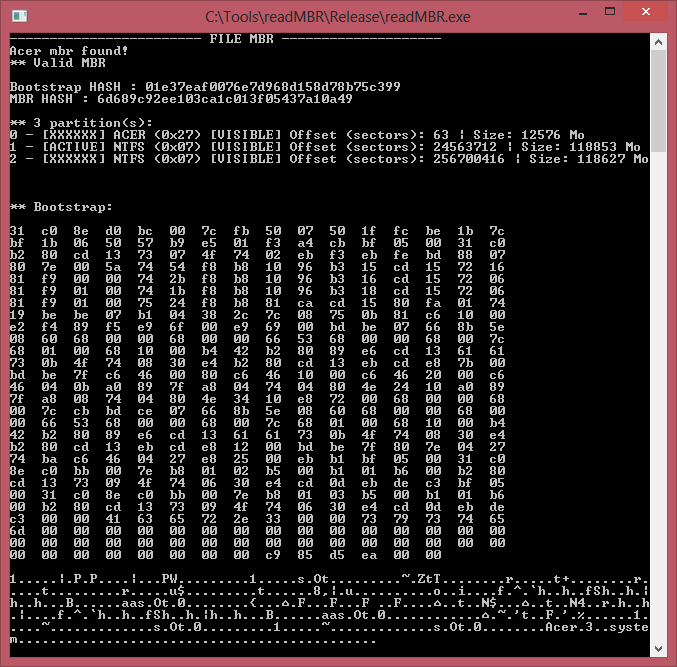
MBRCheck warns about non-standard or infected MBR but is it just Acer's proprietary MBR code (the computer is made by Acer)? Googling the SHA1 checksum gives lots of topics from various support forums where some people suggest replacing with a standard Windows boot code but some just ignore it.
Sending the dumped MBR to Virustotal results in one alert from VBA32, "suspected of Unknown.BootVirus".
I tried to look at the dump using a hex editor and IDA but didn't have much success with the boot code part. Partition table seems to be OK, no signs of partitions created by malware (mainly those TDL-4 variants).
Partition table seems to be OK, no signs of partitions created by malware (mainly those TDL-4 variants).
Dump attached as 7-zipped archive, password 12345
MBRCheck warns about non-standard or infected MBR but is it just Acer's proprietary MBR code (the computer is made by Acer)? Googling the SHA1 checksum gives lots of topics from various support forums where some people suggest replacing with a standard Windows boot code but some just ignore it.
Size Device Name MBR StatusTDSSKiller doesn't find anything, GMER hangs during scan. Combofix doesn't find anything special.
--------------------------------------------
232 GB \\.\PhysicalDrive0 Unknown MBR code
SHA1: 75374D27B77E61C9316E27BACDEE41C1E2C9874E
Found non-standard or infected MBR.
Sending the dumped MBR to Virustotal results in one alert from VBA32, "suspected of Unknown.BootVirus".
I tried to look at the dump using a hex editor and IDA but didn't have much success with the boot code part.
Dump attached as 7-zipped archive, password 12345
Attachments
(480 Bytes) Downloaded 35 times