Hi dcmorton,
First thx for your fast replay and sorry for the vague request.
I will try to explain my self better :)
Andromeda is a bot (AFAIK it is similar to Zeus and Spyeye, also a modularized program which can be functionally developed and supported using plug-ins.) that one of his final payloads is the sample you have sent me.
http://www.maikmorgenstern.de/wordpress/?tag=botnets
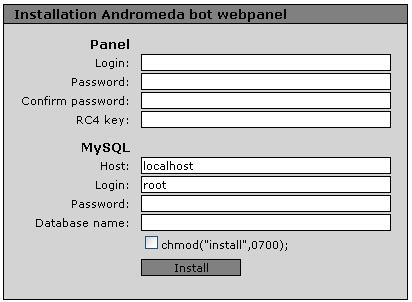
Check the attached SC - the bot webpanel.
1.JPG (20.69 KiB) Viewed 2465 times
BTW, I think I have heard about google somewhere :) - he returned nothing interesting regarding this sample.
dcmorton wrote:p4r4n0id wrote:Hi Guys,
I am looking for a relatively new sample (AFAIK :)) - Andromeda bot. Anyone?
Thx,
p4r4n0id
Well here's the best I can do with an incredibly vague request IMO. Might be what you're looking for, might not be
Google is your friend btw.. I went from vague name "Andromeda bot" to actual name "Worm:Win32/Gamarue.A/B" to VirusTotal result with MD5 to finding a sample of the MD5 using nothing but Google.
Thanks to Kobayashi from vxheavens for the sample as well
Edit:
The sample in the attach is Gamarue.B. MD5 for a Gamarue.A sample is 4a64dd57fbfe0acdf700709b38bd8e69
Keep Low. Move Fast. Kill First. Die Last. One Shot. One Kill. No Luck. Pure Skill.
http://p4r4n0id.com/