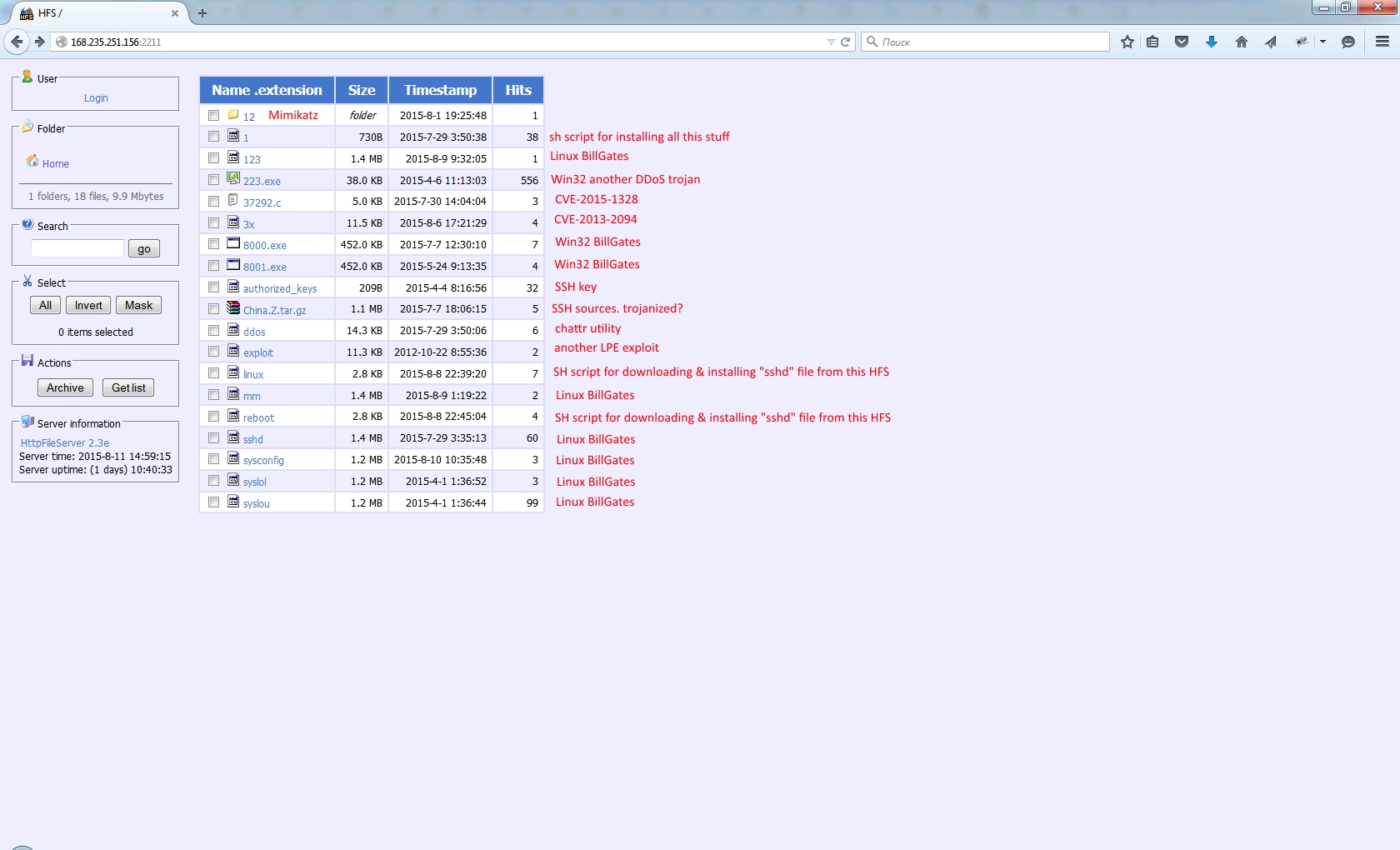
Attacker (SSH): 111.73.46.231
CNC: http://qian.333u.net (122.10.112.193) port: 12027
Sample: https://www.virustotal.com/en/file/d17f ... 437203608/
panel:

CNC: http://qian.333u.net (122.10.112.193) port: 12027
Sample: https://www.virustotal.com/en/file/d17f ... 437203608/
panel:

Attachments
7z / infected
(427.34 KiB) Downloaded 44 times
(427.34 KiB) Downloaded 44 times