Thanks for sharing. This is updated Sirefef with new survival strategy.
Major changes:
1) All MS Cabinet related code removed. Each component (even 2Kb bootstrap lists) are now compressed with APLib;
2) Different startup locations used, no more RECYCLE folder.
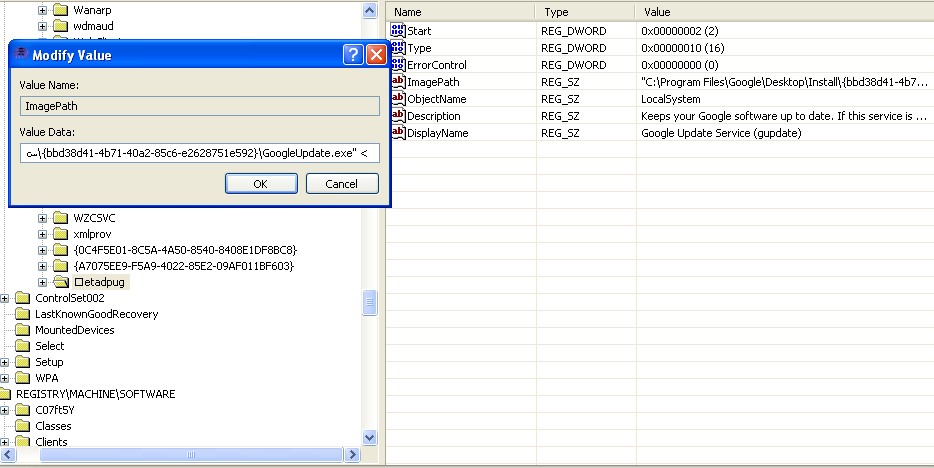
a) Registers itself as a service (primary launch)
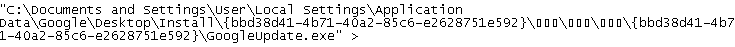
Notice specially crafted symbols in path - SysInternals Autoruns will fail to operate with them, same for Regedit. Since they all use WinAPI to access data, they will fail to open key.
For both cases - registry keys security permissions are broken to prevent access/removal. Same for directories with malware on disk.
Removal.
For (A) - go to PROGRAMFILES\Google\Desktop\Install, take ownership (replacing ALL access list) and erase directory.
Note: Sirefef config file - @ maybe be opened with exclusive access rights. Run Process Explorer, locate "@" (w/o quotes) in "Find Handle or Dll" and close handle. If it still busy - rename it. Reboot computer.
For (B) - go to USERPROFILE\Local Settings\Application Data\Google, take ownership over malware directory and erase it. Reboot computer. After reboot crafted startup entry still will be in registry. Unfortunately regedit cannot handle it. Remove whole "Run" key.
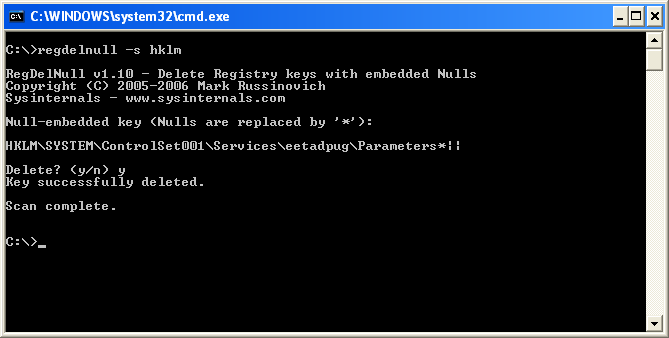
About unaccessible keys/directories (in case of (B)).
This is temporary solution as I don't know any third party tools that able to handle such registry entries and obviously cannot advice internal tool which screenshot you see above. There is nothing impossible here, you just need a tool that is able to handle registry/file path in Native format.
Unpacked, extracted binaries of above Sirefef + three plugins it downloaded in attach.
Major changes:
1) All MS Cabinet related code removed. Each component (even 2Kb bootstrap lists) are now compressed with APLib;
2) Different startup locations used, no more RECYCLE folder.
a) Registers itself as a service (primary launch)
Code: Select all
b) HKCU\Software\Microsoft\Windows\CurrentVersion\Run (reserve launch) if (NT_SUCCESS(( ZwSetValueKey(hKey, &usObjectName, 0, 1, L"LocalSystem", 24))
&& (NT_SUCCESS(ZwSetValueKey(
hKey,
&usDescription,
0,
1,
L"Keeps your Google software up to date. If this service is disabled or stopped, your Google software will not be kept up to date, meaning security vulnerabilities that may arise cannot be fixed and features may not work. This service uninstalls itself when there is no Google software using it.",
588)))
&& NT_SUCCESS(ZwSetValueKey(hKey, &usDisplayName, 0, 1, L"Google Update Service (gupdate)", 64)) )Notice specially crafted symbols in path - SysInternals Autoruns will fail to operate with them, same for Regedit. Since they all use WinAPI to access data, they will fail to open key.
For both cases - registry keys security permissions are broken to prevent access/removal. Same for directories with malware on disk.
Removal.
For (A) - go to PROGRAMFILES\Google\Desktop\Install, take ownership (replacing ALL access list) and erase directory.
Note: Sirefef config file - @ maybe be opened with exclusive access rights. Run Process Explorer, locate "@" (w/o quotes) in "Find Handle or Dll" and close handle. If it still busy - rename it. Reboot computer.
For (B) - go to USERPROFILE\Local Settings\Application Data\Google, take ownership over malware directory and erase it. Reboot computer. After reboot crafted startup entry still will be in registry. Unfortunately regedit cannot handle it. Remove whole "Run" key.
About unaccessible keys/directories (in case of (B)).
This is temporary solution as I don't know any third party tools that able to handle such registry entries and obviously cannot advice internal tool which screenshot you see above. There is nothing impossible here, you just need a tool that is able to handle registry/file path in Native format.
Unpacked, extracted binaries of above Sirefef + three plugins it downloaded in attach.
Attachments
pass: infected
(148.97 KiB) Downloaded 161 times
(148.97 KiB) Downloaded 161 times
Ring0 - the source of inspiration