i told you, it not working. No infected services at all. code from your attach i can extract from dropper (file w32 from cab archive). i'm interested in extended attribute data. can you attach it please :?:
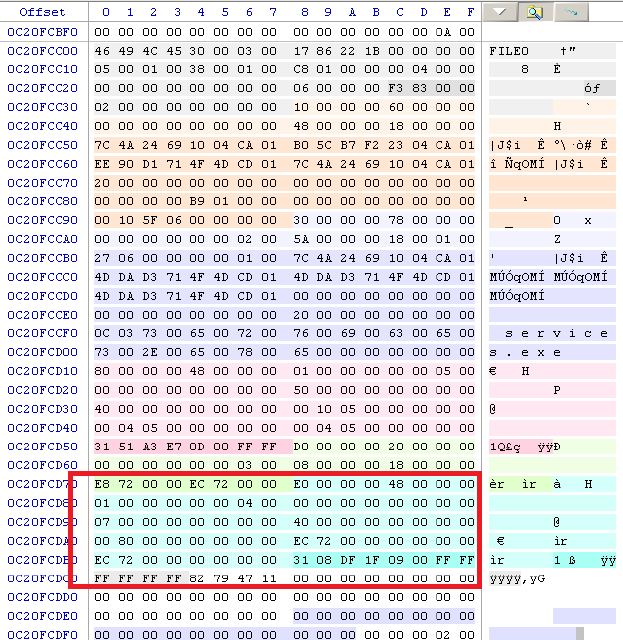
kmd wrote:i told you, it not working. No infected services at all. code from your attach i can extract from dropper (file w32 from cab archive). i'm interested in extended attribute data. can you attach it please :?:Ea data in x32 infected case is a e32 file from payload that posted before http://www.kernelmode.info/forum/viewto ... 390#p13959, with size of 22 892 bytes.
In attach cutted PE from this Ea.
19/41 https://www.virustotal.com/file/50ddaa6 ... /analysis/