What a nice combo! 
Dropper(Signed) = Main module(Signed) + Rootkit
String(s)
Dropper(Signed): VT 28/41 https://www.virustotal.com/file/1e7b501 ... 339162109/
Main module(Signed): VT 21/42 https://www.virustotal.com/file/f4f27fa ... 339162451/
Rootkit: VT 34/42 https://www.virustotal.com/file/eb0d5a7 ... 339162579/
Dropped exe(Signed): VT 0/42 https://www.virustotal.com/file/a532f05 ... 339162700/
Old samples...
VT 7/43 https://www.virustotal.com/file/b0c579d ... /analysis/
VT 11/43 https://www.virustotal.com/file/1f64dd7 ... /analysis/
VT 16/43 https://www.virustotal.com/file/63391e6 ... /analysis/
Dropper(Signed) = Main module(Signed) + Rootkit
String(s)
Code: Select all
VirusTotal result(s)SetSecurityDescriptorControl
advapi32.dll
AddAccessAllowedAceEx
\Drivers
%s\%d_res.tmp
LocalService_0x%d
LocalService
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
.PAX
.PAD
FILE
HI1.DLL
ServiceMain
ClientMain
ServiceDll
\Parameters
Description
SYSTEM\CurrentControlSet\Services\%s
CreateService(Parameters)
%SystemRoot%\System32\svchost.exe -k LocalService
MACHINE\SYSTEM\CurrentControlSet\Services\%s
%s\HI1.DLL
OpenSCManager()
RegQueryValueEx(Svchost\LocalService)
Windows Driver
%s\HI2.DLL
LocalService_0x0
FILE2
HI2.DLL
%s\hi.ini
InstallModule
Microsoft Windows
Update
2008
2003
2000
Vista
ProductName
SOFTWARE\Microsoft\Windows NT\CurrentVersion
...
svchost.dll
ClientMain
.PAX
.PAD
bad Allocate
bad buffer
Mozilla/4.0 (compatible)
C:\WINDOWS\TEMP\%d%d%d%d.ccc
%s?abc=%d%d%d%d
C:\Del.bat
Del c:\windows\temp\**.ccc
Del %0
GET %s HTTP/1.0
Accept: image/gif, image/x-xbitmap, image/jpeg, image/chpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */*
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
If-Modified-Since: Sun, 11 Jun 2008 11:22:33 GMT
If-None-Match: "60794-12b3-e4169440"
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322; .NET CLR 1.0.3705)
Host:%s
http://
\Program Files\Internet Explorer\IEXPLORE.EXE
"%s" "%s?abc=%d%d%d%d"
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET4.0C; .NET4.0E)
InternetOpenUrlA
InternetOpenA
InternetCloseHandle
WININET.dll
GET /%s HTTP/1.1
Accept: application/x-shockwave-flash, image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, application/xaml+xml, application/x-ms-xbap, application/x-ms-application, application/QVOD, application/QVOD, */*
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE %u.0; Windows NT %u.1; SV1; .NET4.0C; .NET4.0E; TheWorld)
Host: %s
Connection: Keep-Alive
%s:%u
%d.%d.%d.%d
www.%s
%s.com
SYSTEM\CurrentControlSet\Services\%s
InstallModule
Type
SYSTEM\CurrentControlSet\Services\
RegQueryValueEx(Type)
WinSta0\Default
\Mark.ini
Host
2008
2003
2000
ProductName
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\DNM.ini
\DN.ini
\UDM.ini
\UD.ini
\SYM.ini
\SY.ini
\SPM.ini
\SP.ini
\ICM.ini
\IC.ini
kernel32.dll
%-24s %-15s
REG_BINARY
%-24s %-15s 0x%x(%d)
REG_DWORD
REG_MULTI_SZ
%-24s %-15s %s
REG_SZ
REG_EXPAND_SZ
[%s]
XXX.DLL
XXX.DLL
%s\hi.ini
\cmd.exe
...
www.mehome1.com
www.mehome2.com
www.mehome3.com
www.meserver1.com
www.meserver2.com
www.fz0575.com
www.af0575.com
www.wk1888.com
1:%s
http://%s:2011/%d.exe?=%d
2:%s
http://%s:2011/%dv.exe?=%d
%d%d%d.exe
%s %s
.xvx
~MHz
HARDWARE\DESCRIPTION\System\CentralProcessor\0
Null
\\.\K_HIDE_MODULE
FILE2
FILE
Microsoft Windows
Client\Client %d
winsta0
LocalService_0x0
Process32First
...
Driver Loaded Successfully...
Hide Pid :%u
Hide IP :%u
Hide File:%s
Hide Svc :%ws
Recv Bytes:%u
Struct Bytes:%u
This is HideDirFile!
services.exe
XXX.DLL
XXX.DLL
KeServiceDescriptorTable
ExFreePoolWithTag
swprintf
ExAllocatePoolWithTag
RtlCompareUnicodeString
_except_handler3
RtlImageDirectoryEntryToData
DbgPrint
PsGetVersion
ZwQueryDirectoryFile
ZwDeviceIoControlFile
ZwQuerySystemInformation
IoDeleteDevice
IoCreateSymbolicLink
IoCreateDevice
RtlInitUnicodeString
IofCompleteRequest
RtlFreeAnsiString
RtlCompareMemory
RtlUpperString
RtlUnicodeStringToAnsiString
RtlInitAnsiString
KeDetachProcess
_wcsicmp
ProbeForRead
KeAttachProcess
IoGetCurrentProcess
ntoskrnl.exeDropper(Signed): VT 28/41 https://www.virustotal.com/file/1e7b501 ... 339162109/
Main module(Signed): VT 21/42 https://www.virustotal.com/file/f4f27fa ... 339162451/
Rootkit: VT 34/42 https://www.virustotal.com/file/eb0d5a7 ... 339162579/
Dropped exe(Signed): VT 0/42 https://www.virustotal.com/file/a532f05 ... 339162700/
Old samples...
VT 7/43 https://www.virustotal.com/file/b0c579d ... /analysis/
VT 11/43 https://www.virustotal.com/file/1f64dd7 ... /analysis/
VT 16/43 https://www.virustotal.com/file/63391e6 ... /analysis/
Attachments
pass: malware
(147.38 KiB) Downloaded 76 times
(147.38 KiB) Downloaded 76 times
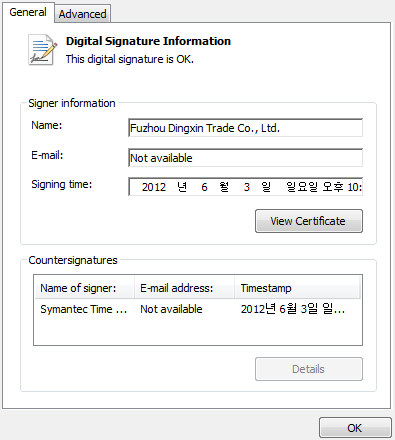
cert.png (14.94 KiB) Viewed 3122 times