Dropper
MD5: 1cb27d4ecd25c2030ebb6a1a9b7e3321
SHA1: 8d502546c344a16c66ff4ee82dda3004343d3ff9
33 / 42 https://www.virustotal.com/file/83230bd ... /analysis/
Dropped:
function hooking for hide autostart keys and files in appdata
and PEB-hiding


MD5: 1cb27d4ecd25c2030ebb6a1a9b7e3321
SHA1: 8d502546c344a16c66ff4ee82dda3004343d3ff9
33 / 42 https://www.virustotal.com/file/83230bd ... /analysis/
Dropped:
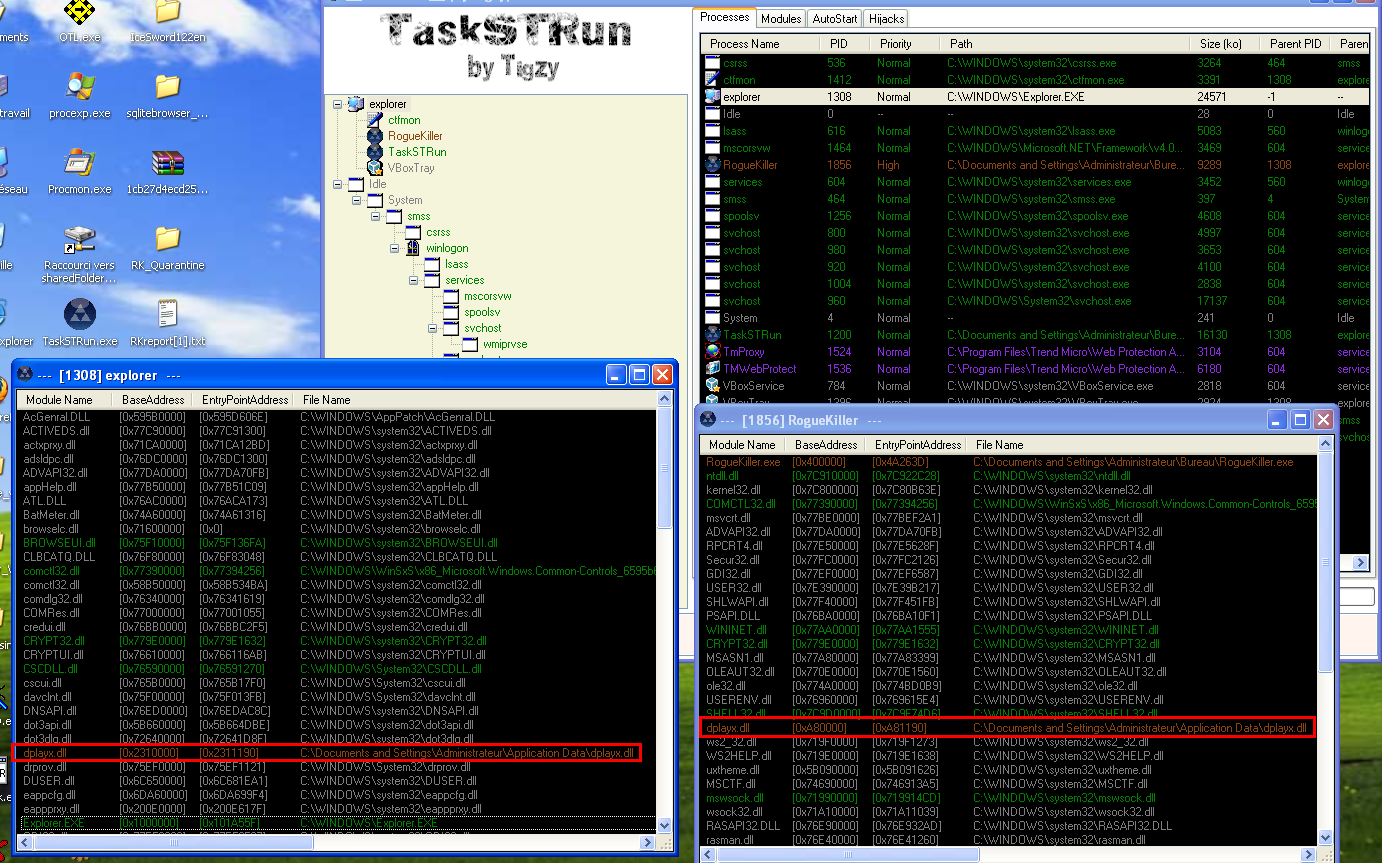
%appdata%\dplaysvr.exe -> MD5: 71d1aaf8150ae6b2ffa60b241d84b365Autorun from:
%appdata%\dplayx.dll -> MD5: ebe71d129858f2f5e9fd81940b25d251
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\dplaysvrModifies hosts:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\dplaysvr
94.63.147.16 hxxp://www.google.comContains user mode "rootkit" functionality (infects processes in memory):
94.63.147.17 hxxp://www.bing.com
function hooking for hide autostart keys and files in appdata
and PEB-hiding
Attachments
pass:infected
(155.49 KiB) Downloaded 56 times
(155.49 KiB) Downloaded 56 times
pass:infected
(45.11 KiB) Downloaded 52 times
(45.11 KiB) Downloaded 52 times
pass:infected
(28.77 KiB) Downloaded 54 times
(28.77 KiB) Downloaded 54 times