DMA Locker 4.0 found at hxxp://80.87.205.115/2/bbv.exe
Attachments
(154.17 KiB) Downloaded 75 times
A forum for reverse engineering, OS internals and malware analysis
dma2004@zerobit.email
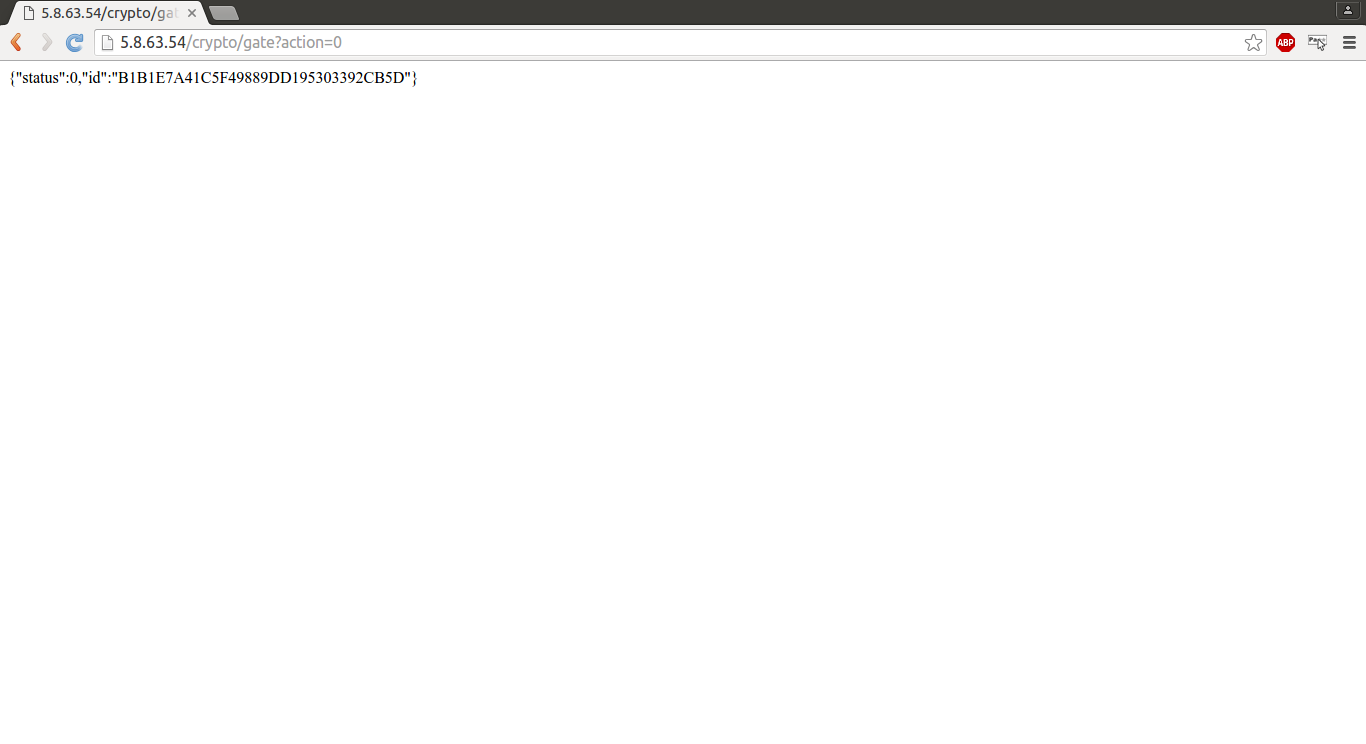
http://5.8.63.54/crypto/gate?action=0
http://5.8.63.54/crypto/client_payment_instructions?botId=B1B1E7A41C5F49889DD195303392CB5D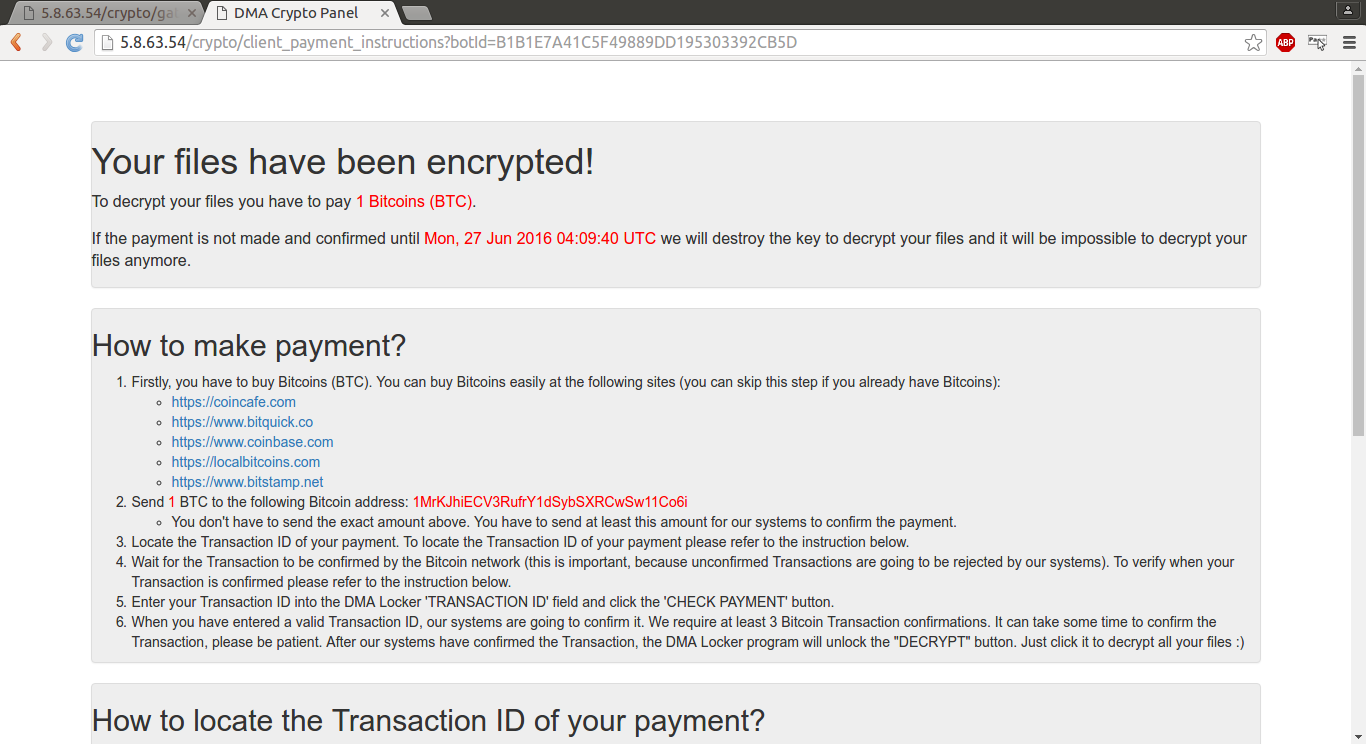

Today's campaign details, picture and etc report is here: http://imgur.com/a/CZKztFinally could run it well : <Screenshot> <Screenshot> <Screenshot>
Domains : actioncompass.online
BTC: 16hHkyuzCDRFzoejVuqajqrnbmKHSmEfQM
Emails: dma4004@zerobit.email and team4004@gmx.com
{
"ip": "5.8.63.31",
"hostname": "No Hostname",
"city": "Saint Petersburg",
"region": "St.-Petersburg",
"country": "RU",
"loc": "59.8944,30.2642",
"org": "AS29182 JSC ISPsystem",
"postal": "190808"
}http://actioncompass.online/crypto/client_payment_instructions?botId=%s
http://%s/crypto/client_free_decrypt?botId=%s
http://%s/crypto/client_payment_instructions?botId=%s
GET /crypto/gate?action=0 HTTP/1.1
GET /crypto/gate?action=1&botId=%s HTTP/1.1
GET /crypto/gate?action=5&botId=%s HTTP/1.1
GET /crypto/gate?action=2&botId=%s HTTP/1.1
GET /crypto/gate?action=3&botId=%s HTTP/1.1
GET /crypto/gate?action=4&botId=%s&transactionId=%s HTTP/1.1
GET /crypto/gate?action=6&botId=%s HTTP/1.1
unixfreaxjp wrote: cc: @EP_X0FF @Xylit0l you both must see the loader part..Nothing interesting, its just obfuscated loader which runs main ransom hardcoded executable from %temp% multiple times until it finally starts normally. What a trash.
EP_X0FF wrote:Nothing interesting, its just obfuscated loader which runs main ransom hardcoded executable from %temp% multiple times until it finally starts normally. What a trash.Thank you.
sysopfb wrote: Was also seeing cerber from these but the actor switched to DMA locker it seems?Yes, I was informed also It switched also to Cerber in the DMA initial url(below), the actor played double version of ransomware:
hxxp://avtomatika-dv[.]ru/image/data/avatars/.../log.php?f=404
hxxp://www[.]harmanhouse[.]com/catalog/language/english/error/.../log.php?f=404
h00p://irinahair.ru/.../log.php=404