Hi USForce,
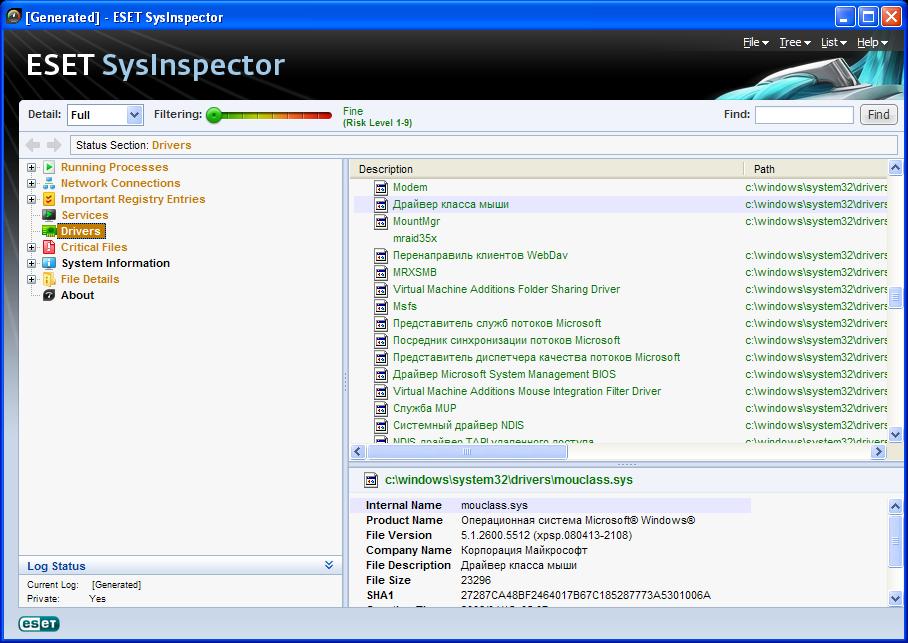
TDL3 installed by dogma.exe (from post above) is totally undetected by SysInspector.
It is running under Virtual PC and shows nothing.
Infected driver is mouclass.sys
Other interesting fact - last update of SysInspector was before TDL3 ITW active launch.
Last updated on: 7.10.2009
So it's very out-dated and can't detect something like TDL3 by design.
RkU Version: 5.1.709.2270, Type VX2 (VX+)
==============================================
OS Name: Windows XP
Version 5.1.2600 (Service Pack 3)
Number of processors #1
==============================================
0x81DBFCC4 Page with executable code, size: 4096 bytes
0x81471291 Page with executable code [ ETHREAD 0x81FC4030 ] TID: 40, size: 3439 bytes
0x81470E25 Page with executable code [ ETHREAD 0x81FC4030 ] TID: 40, size: 475 bytes
0x81471024 Page with executable code [ ETHREAD 0x81FC4030 ] TID: 40, size: 4060 bytes
0x81DBC0B2 Page with executable code [ ETHREAD 0x81FC4610 ] TID: 56, size: 3918 bytes
0x81DBF6AE Page with executable code [ ETHREAD 0x81FC4610 ] TID: 56, size: 2386 bytes
0x81DC1D74 Page with executable code [ ETHREAD 0x81FC4610 ] TID: 56, size: 652 bytes
0xF8810000 WARNING: Virus alike driver modification [mouclass.sys] :: 0xF8814814, size: 24576 bytes
As fact I believe it just detect VBox driver. Perhaps it simple coincidence. This can be proven by taking a short test on VmWare of VPC.
edit:
SysInspector highlighted Rootkit Unhooker driver in yellow, probably because it was not on disk.
Regards.