rkhunter wrote:Hmm... that is all I was told. I have a copy of Sirefef.P dropper perhaps it will download this n64 payload at some point if I am patient enough, because the VT link you posted looks like what I am after. Thanks,FoolishTech wrote:Does anyone have a sample of Sirefef.Y (as reported by MSE)?? Haven't managed to catch it myself, but I'm told that it (either by itself or perhaps with a botched removal attempt) would put Windows in an infinite reboot loop with about 60 seconds of desktop time before the reboot - and that shutdown -a will not abort it. Anyone heard of this or is it likely a different malware payload downloaded by the Sirefef infection causing this?Do you have a more accurate name? "Sirefef.Y" as I remember there is no droppers with such name. Actual droppers detected by it as Trojan:Win32/Sirefef.P.
If you mean Trojan:Win64/Sirefef.Y, for example, https://www.virustotal.com/file/073b1f9 ... /analysis/ - this is payload n64 from dropper container that was posted before.
A forum for reverse engineering, OS internals and malware analysis
@FoolishTech
plz give us a dropper
------------
http://r.virscan.org/af84450824ea9a75f9f13ab2bc7b24fd
:lol: :roll:
2 weeks and all this "industry" with all this Mikko's, security experts fails to detect virus :))
plz give us a dropper
------------
http://r.virscan.org/af84450824ea9a75f9f13ab2bc7b24fd
:lol: :roll:
2 weeks and all this "industry" with all this Mikko's, security experts fails to detect virus :))
Damn epic...
infected services.exe on x32 - 2 / 42 - Virus:Win32/Sirefef.R https://www.virustotal.com/file/4c1096f ... 340263629/
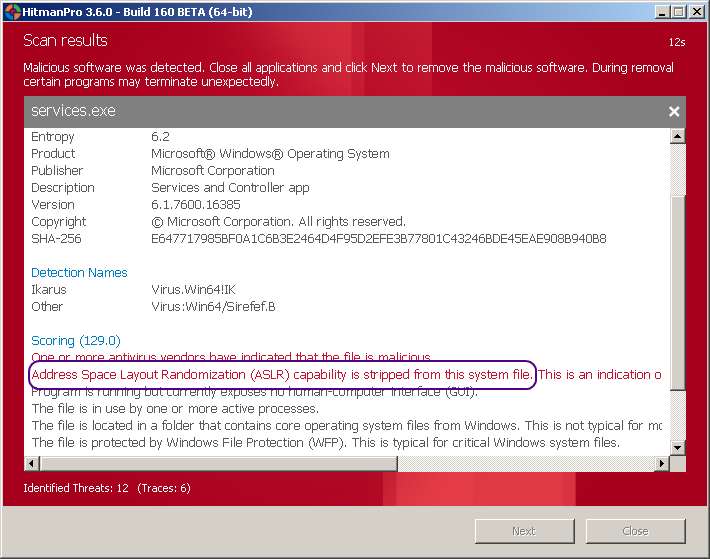
infected services.exe on x64 - 9 / 42 - Virus:Win64/Sirefef.B https://www.virustotal.com/file/e647717 ... 340263662/
PE extracted from e32 - 27 / 42 - Trojan:Win32/Sirefef.P https://www.virustotal.com/file/92532a2 ... 340264328/
PE extracted from e64 - 11 / 42 - Trojan:Win64/Sirefef.M https://www.virustotal.com/file/98d44fc ... 340264859/
Shellcode extracted from e32 - 3 / 42 - Trojan:Win32/Sirefef.AH https://www.virustotal.com/file/bb9695e ... 340265078/
Shellcode extracted from e64 - 2 / 42 - Trojan:Win64/Sirefef.Y https://www.virustotal.com/file/c19dd75 ... 340265355/
n32 component 29 / 42 - Trojan:Win32/Sirefef.P https://www.virustotal.com/file/2c4f807 ... 340265544/
n64 component 31 / 42 - Trojan:Win64/Sirefef.Y https://www.virustotal.com/file/073b1f9 ... 340265554/
infected services.exe on x32 - 2 / 42 - Virus:Win32/Sirefef.R https://www.virustotal.com/file/4c1096f ... 340263629/
infected services.exe on x64 - 9 / 42 - Virus:Win64/Sirefef.B https://www.virustotal.com/file/e647717 ... 340263662/
PE extracted from e32 - 27 / 42 - Trojan:Win32/Sirefef.P https://www.virustotal.com/file/92532a2 ... 340264328/
PE extracted from e64 - 11 / 42 - Trojan:Win64/Sirefef.M https://www.virustotal.com/file/98d44fc ... 340264859/
Shellcode extracted from e32 - 3 / 42 - Trojan:Win32/Sirefef.AH https://www.virustotal.com/file/bb9695e ... 340265078/
Shellcode extracted from e64 - 2 / 42 - Trojan:Win64/Sirefef.Y https://www.virustotal.com/file/c19dd75 ... 340265355/
n32 component 29 / 42 - Trojan:Win32/Sirefef.P https://www.virustotal.com/file/2c4f807 ... 340265544/
n64 component 31 / 42 - Trojan:Win64/Sirefef.Y https://www.virustotal.com/file/073b1f9 ... 340265554/
kmd wrote:2 weeks and all this "industry" with all this Mikko's, security experts fails to detect virus :))They were busy flaming about flame.
Ring0 - the source of inspiration
@FoolishTech
MSE goes into infinite loop when it detects infected services.exe AFTER partial removal. You should be able to recreate this scenario by infecting with the dropper linked below thanks to thisisu
http://www.kernelmode.info/forum/viewto ... 150#p14070
You should use Hitman Pro to attempt to remove the rest of the infection while MSE is installed and that should set you into that infinite loop.
MSE goes into infinite loop when it detects infected services.exe AFTER partial removal. You should be able to recreate this scenario by infecting with the dropper linked below thanks to thisisu
http://www.kernelmode.info/forum/viewto ... 150#p14070
You should use Hitman Pro to attempt to remove the rest of the infection while MSE is installed and that should set you into that infinite loop.
TeamRocketOps wrote:MSE goes into infinite loop when it detects infected services.exe AFTER partial removal.This is correct. MSE fails to remove Sirefef.Y and this is also why you can find MSE's 50,000byte system driver stuck in Drivers section of logs.
Examples (caused by multiple removal fail by MSE)
Code: Select all
Source: http://forums.majorgeeks.com/showthread.php?t=2603871 axqvsxde; \??\C:\Windows\system32\drivers\axqvsxde.sys [x]
1 beaxgerf; \??\C:\Windows\system32\drivers\beaxgerf.sys [x]
1 epvwbckj; \??\C:\Windows\system32\drivers\epvwbckj.sys [x]
1 feetgaza; \??\C:\Windows\system32\drivers\feetgaza.sys [x]
1 hmhdbcgf; \??\C:\Windows\system32\drivers\hmhdbcgf.sys [x]
1 ofdtudxb; \??\C:\Windows\system32\drivers\ofdtudxb.sys [x]
1 sgfntmwz; \??\C:\Windows\system32\drivers\sgfntmwz.sys [x]
1 tgcxrtzb; \??\C:\Windows\system32\drivers\tgcxrtzb.sys [x]
1 urpvvzux; \??\C:\Windows\system32\drivers\urpvvzux.sys [x]Attachments
(35.03 KiB) Downloaded 34 times
This is caused by services.exe termination.
Ring0 - the source of inspiration
Yup, ran into the same thing. When the reboot prompt comes up if you look for services.exe it isn't present anymore as a running process on the infected machine.
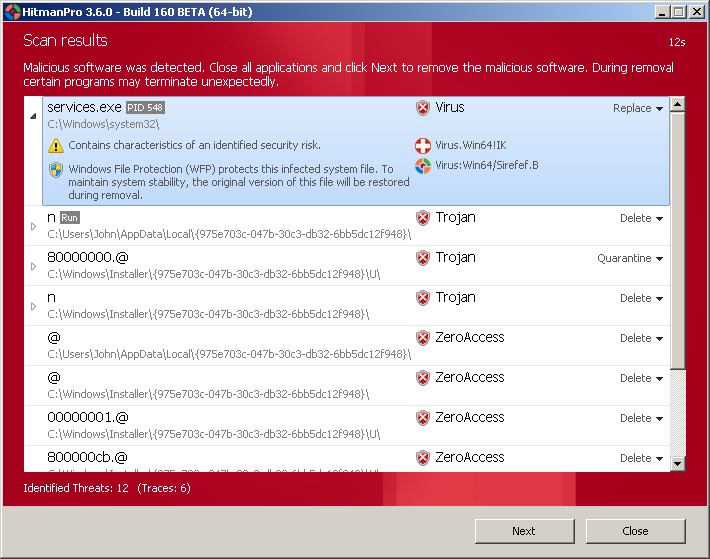
Just posted HitmanPro 3.6 build 160 BETA.
The update is focused primarily on the removal of ZeroAccess/Sirefef services.exe variant:
32-bit http://dl.surfright.nl/HitmanPro36beta.exe
64-bit http://dl.surfright.nl/HitmanPro36beta_x64.exe
The update is focused primarily on the removal of ZeroAccess/Sirefef services.exe variant:
32-bit http://dl.surfright.nl/HitmanPro36beta.exe
64-bit http://dl.surfright.nl/HitmanPro36beta_x64.exe
Erik Loman [HitmanPro]
SurfRight B.V. - www.surfright.com
SurfRight B.V. - www.surfright.com
Very nice, Erik :)