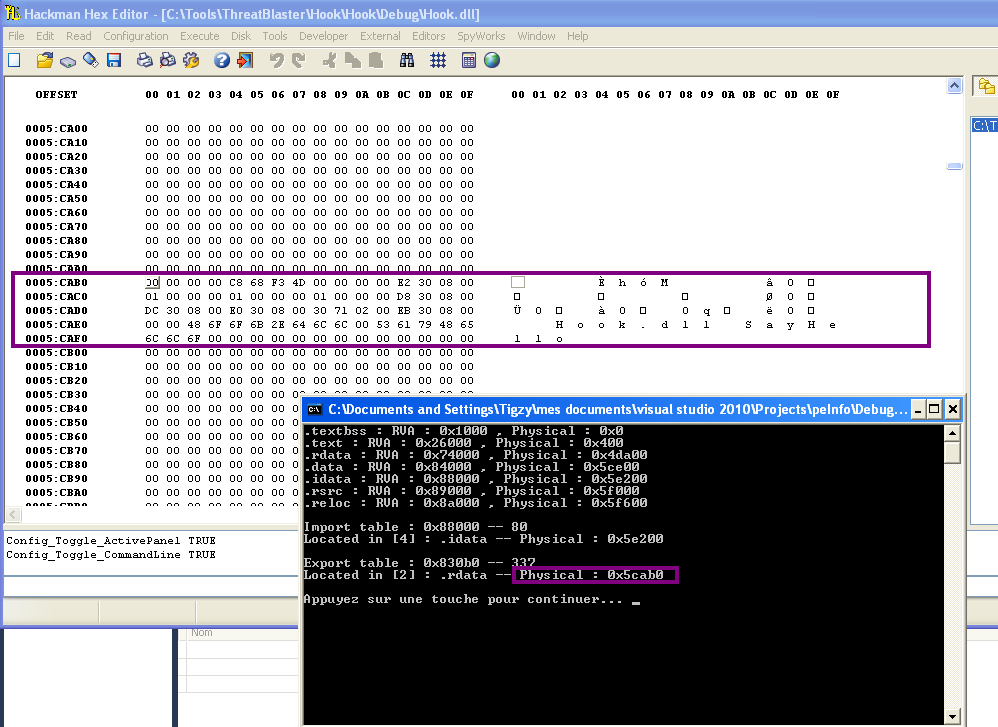
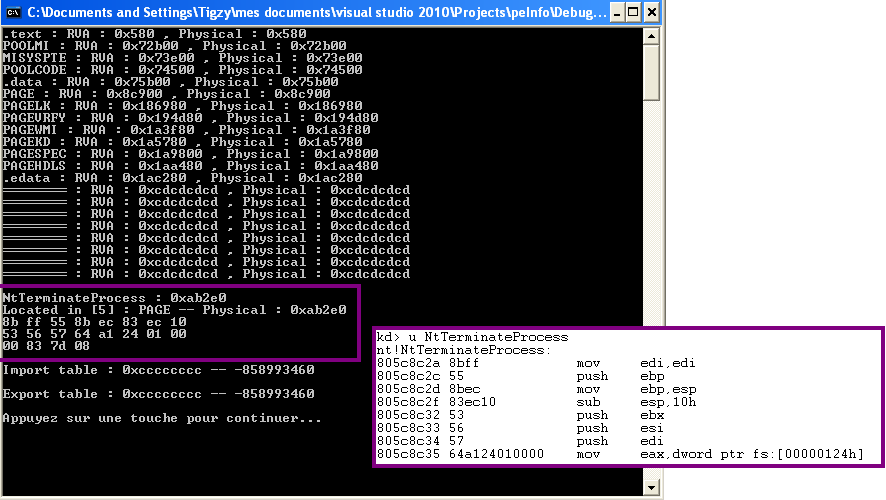
you use the .reloc section to rebase the RVA's. for example in a pe32 the default imagebase is 0x400000. So you could like run across some code in the .text section basically doing:
push 0x403000
call something
which could be pushing the address of a string from .rdata
but that is the offset once the executable is mapped to memory (not in the file). If you read the section headers it tells you the VA (not RVA) of the base of the section (added to base) once loaded to memory. So whereas say .rdata could be at 0x403000, in the file it could be at offset 0x1200 or something.
push 0x403000
call something
which could be pushing the address of a string from .rdata
but that is the offset once the executable is mapped to memory (not in the file). If you read the section headers it tells you the VA (not RVA) of the base of the section (added to base) once loaded to memory. So whereas say .rdata could be at 0x403000, in the file it could be at offset 0x1200 or something.