Inspired by ITW WinNT/Pitou legacy MBR x86-64 bootkit dropper.
Before anything else read this excellent work -> Windows 7 UAC whitelist, read it carefully as it explains everything especially why Windows User Account Control is a big fucken marketing joke from Microsoft just like DSE.
Below is our variant of his work with removal of all C++ trash and adapting different UAC bypass method from WinNT/Pitou (bootkit authors also used as base Leo Davidson work).
The only setting UAC somehow is able to show itself - if they are set on maximum. But here revealed another Microsoft UAC architecture flaw by design - even when it blocks something, it cannot properly determine what it blocked, representing possible malicious actions as taken by Microsoft, facepalm. Will you trust verified Microsoft action with verified digital certificate from Microsoft?
Supported Windows version, all from 7xxx builds up to latest so "confidential" MS build 9901.
Project overview:
Win32 and x64 configurations.
Compiled in MSVS 2013 U4, used pure C, compiled as C++
No additional dependencies.
All libs in attach.
Debug builds configurations present only for debugging stuff not for UAC bypass stage execution (shellcode will be screwed up).
Require Heavens Gate adaptation for proper work from Win32 app under WOW64, if you don't know what is HG then skip this moment.
x64 loader VT
https://www.virustotal.com/en/file/78ca ... 418968668/
x86-32 loader VT
https://www.virustotal.com/en/file/9795 ... 418968812/
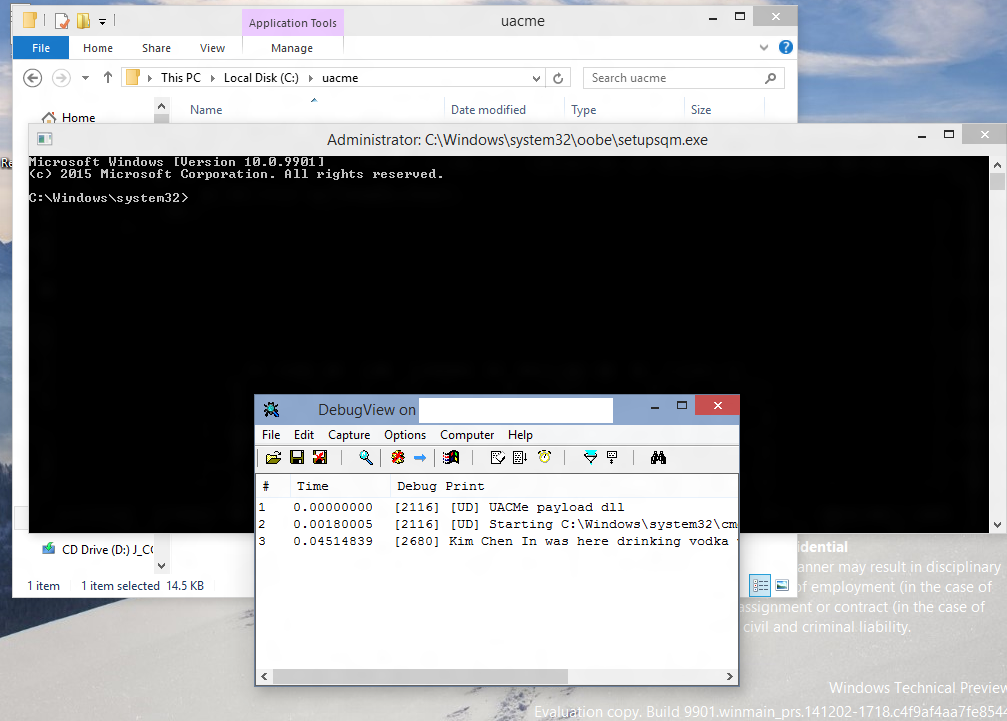
Screeenshots taken from Windows 10 TP build 9901
Before anything else read this excellent work -> Windows 7 UAC whitelist, read it carefully as it explains everything especially why Windows User Account Control is a big fucken marketing joke from Microsoft just like DSE.
Below is our variant of his work with removal of all C++ trash and adapting different UAC bypass method from WinNT/Pitou (bootkit authors also used as base Leo Davidson work).
The only setting UAC somehow is able to show itself - if they are set on maximum. But here revealed another Microsoft UAC architecture flaw by design - even when it blocks something, it cannot properly determine what it blocked, representing possible malicious actions as taken by Microsoft, facepalm. Will you trust verified Microsoft action with verified digital certificate from Microsoft?
Supported Windows version, all from 7xxx builds up to latest so "confidential" MS build 9901.
Project overview:
Win32 and x64 configurations.
Compiled in MSVS 2013 U4, used pure C, compiled as C++
No additional dependencies.
All libs in attach.
Debug builds configurations present only for debugging stuff not for UAC bypass stage execution (shellcode will be screwed up).
Require Heavens Gate adaptation for proper work from Win32 app under WOW64, if you don't know what is HG then skip this moment.
x64 loader VT
https://www.virustotal.com/en/file/78ca ... 418968668/
x86-32 loader VT
https://www.virustotal.com/en/file/9795 ... 418968812/
Screeenshots taken from Windows 10 TP build 9901
Last edited by EP_X0FF on Sun Mar 29, 2015 8:48 am, edited 1 time in total.
Reason: removed attach, see http://www.kernelmode.info/forum/viewtopic.php?p=25523#p25523 for more info
Ring0 - the source of inspiration