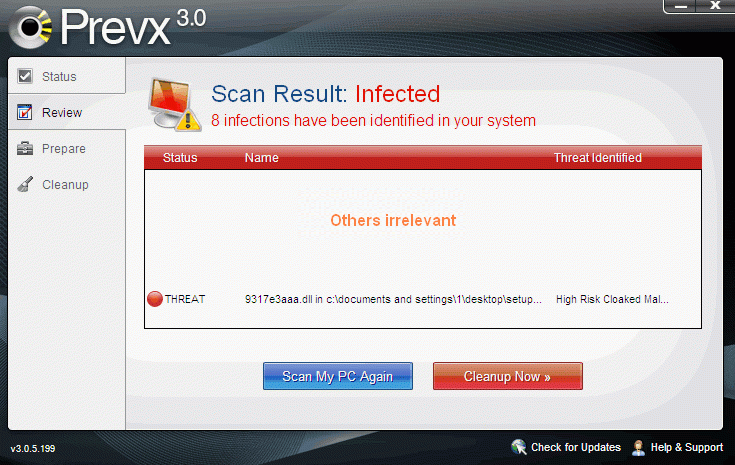
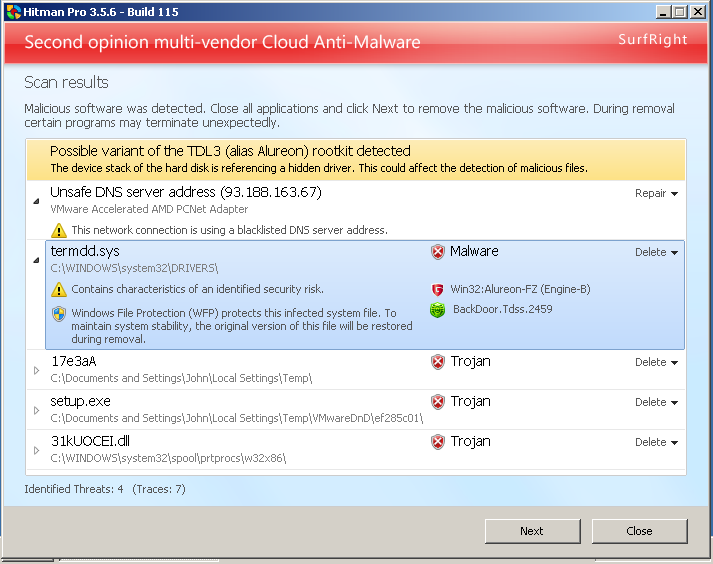
Well, I see no problems with this version.
They added back loading "easter egg" btw :)
"Put your signature here" from drvXX.
And as previous it still renders my test machine with XP to unbootable state after infection.
They added back loading "easter egg" btw :)
"Put your signature here" from drvXX.
And as previous it still renders my test machine with XP to unbootable state after infection.
Ring0 - the source of inspiration