Hello,
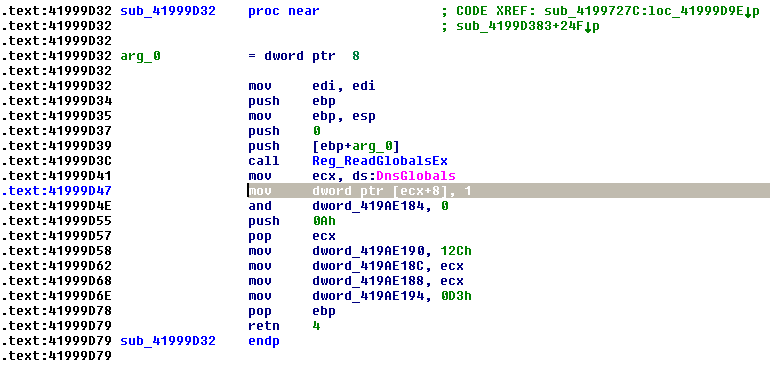
I've stumbled upon a DLL, which has an exported structure, mainly the dnsapi.dll module exporting the DnsGlobals structure. While creating the proxy DLL dnsapi.dll and forwarding function calls to the original DLL dnsapi_.dll (renamed from dnsapi.dll in system32), I'm a little worried how I should approach the problem. The problem is that some functions in other DLLs access the DnsGlobals structure directly, reading/writing values from it. Since I'm using a proxy DLL; those reads/writes go directly to my proxy DLL and not the original DLL. Therefore, the external DLLs would change the structure in the proxy dll dnsapi.dll and not in the original dll dnsapi_.dll, which could result in an inconsistency, because an external DLL changes the structure in proxy DLL and then calls a function that gets forwarded to the original DLL, which doesn't have that structure (but has it's own copy that wasn't changed).
I could solve the problem the following ways:
1. I could create my own structure in the proxy DLL, but the structure could get read from/written to directly from other DLLs (since it's exported). Besides read/write operations (DATA XREFs in Ida Pro are labeled as 'r' and 'w'), there are also address XREFS of type 'o', which hold a pointer to an address. Therefore, not only the current exported structure, but also all dependent structures are affected.
2. Change the While loading the original dll dnsapi_.dll from the DllMain of the current dll dnsapi.dll, I could get the address of the DnsGlobals structure and copy the already initialized structure (since DllMain was called when we called LoadLibrary) from the original DLL (obtain the address with GetProcAddress). By doing it this way, if we pass some call through our proxy DLL to the original DLL; it's functions are changing the dnsglobals structure in the original DLL (but not in proxy dll). To solve that we would need to copy-paste the changes from the original dnsglobals structure to the proxy dnsglobal structure every time a function changes them, to keep them in sync.
3. While loading the original dll dnsapi_.dll from the DllMain of the current dll dnsapi.dll, I could get the address of the DnsGlobals structure and replace the address in current proxy DLL with the address of the original DnsGlobals structure. I don't see any dowsides with this, so I'm thinking this is the way to go.
Any ideas, comments on my thinking (especially the number 3., which I think is the way to go with exported data structures).
I've stumbled upon a DLL, which has an exported structure, mainly the dnsapi.dll module exporting the DnsGlobals structure. While creating the proxy DLL dnsapi.dll and forwarding function calls to the original DLL dnsapi_.dll (renamed from dnsapi.dll in system32), I'm a little worried how I should approach the problem. The problem is that some functions in other DLLs access the DnsGlobals structure directly, reading/writing values from it. Since I'm using a proxy DLL; those reads/writes go directly to my proxy DLL and not the original DLL. Therefore, the external DLLs would change the structure in the proxy dll dnsapi.dll and not in the original dll dnsapi_.dll, which could result in an inconsistency, because an external DLL changes the structure in proxy DLL and then calls a function that gets forwarded to the original DLL, which doesn't have that structure (but has it's own copy that wasn't changed).
I could solve the problem the following ways:
1. I could create my own structure in the proxy DLL, but the structure could get read from/written to directly from other DLLs (since it's exported). Besides read/write operations (DATA XREFs in Ida Pro are labeled as 'r' and 'w'), there are also address XREFS of type 'o', which hold a pointer to an address. Therefore, not only the current exported structure, but also all dependent structures are affected.
2. Change the While loading the original dll dnsapi_.dll from the DllMain of the current dll dnsapi.dll, I could get the address of the DnsGlobals structure and copy the already initialized structure (since DllMain was called when we called LoadLibrary) from the original DLL (obtain the address with GetProcAddress). By doing it this way, if we pass some call through our proxy DLL to the original DLL; it's functions are changing the dnsglobals structure in the original DLL (but not in proxy dll). To solve that we would need to copy-paste the changes from the original dnsglobals structure to the proxy dnsglobal structure every time a function changes them, to keep them in sync.
3. While loading the original dll dnsapi_.dll from the DllMain of the current dll dnsapi.dll, I could get the address of the DnsGlobals structure and replace the address in current proxy DLL with the address of the original DnsGlobals structure. I don't see any dowsides with this, so I'm thinking this is the way to go.
Any ideas, comments on my thinking (especially the number 3., which I think is the way to go with exported data structures).